The State of Ransomware in 2022
Outpost24
MAY 15, 2022
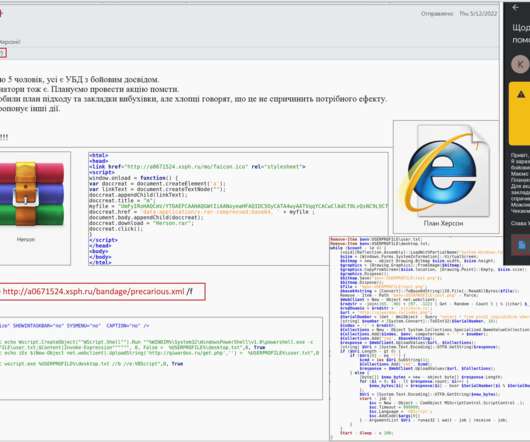
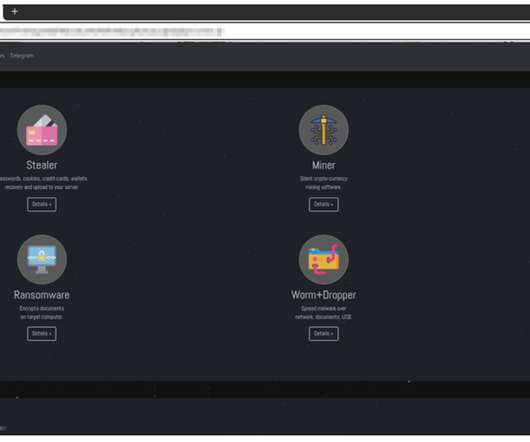
The State of Ransomware in 2022. 17.May.2022. Florian Barre. Mon, 05/16/2022 - 01:10. Blueliv, an Outpost24 company. Threat Intelligence. Teaser. Ransomware continues to be a prevalent threat to almost every modern industry after a sudden renaissance at the beginning of the COVID-19 pandemic as threat actors sought to capitalize on overwhelmed organizations and their suddenly vulnerable employees.













Let's personalize your content