Stolen Zoom Credentials: Hackers Sell Cheap Access
Data Breach Today
APRIL 16, 2020
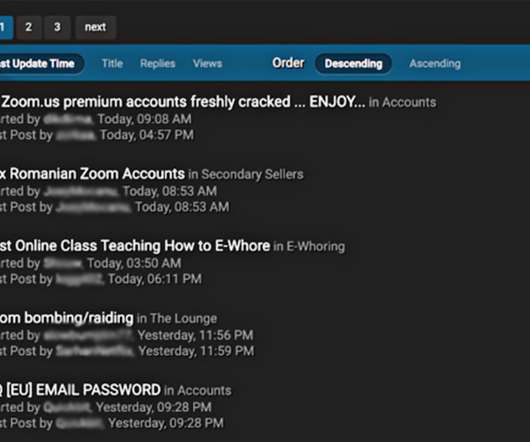
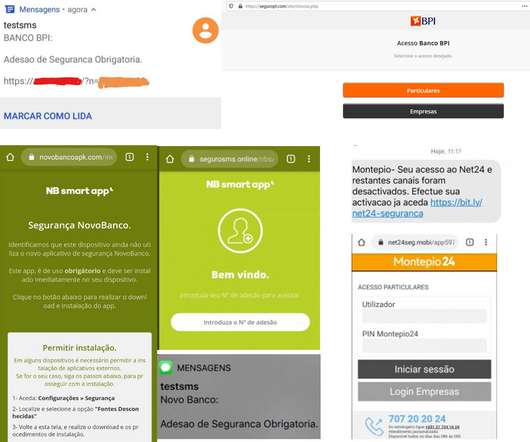
Meanwhile, Zoom Continues Security Overhaul With Bug-Bounty Reboot, Geo-Fencing One measure of the popularity of the Zoom teleconferencing software: Cybercrime forums are listing an increasing number of stolen accounts for sale, which attackers could use to "Zoom bomb" calls and push malicious files to meeting participants. Security experts describe essential defenses.






































Let's personalize your content