Cybersecurity Leadership: Fighting Back Against Fraud
Data Breach Today
DECEMBER 11, 2020
CEOS and CISOs on Responding to the Multichannel Fraud Spike Fraud explodes in tough times, and do times come any tougher than they have with COVID-19? In this latest Cybersecurity Leadership panel, CEOs and CISOs describe their efforts to spot and stop emerging fraud schemes involving synthetic IDs, social engineering and greater insider risks.


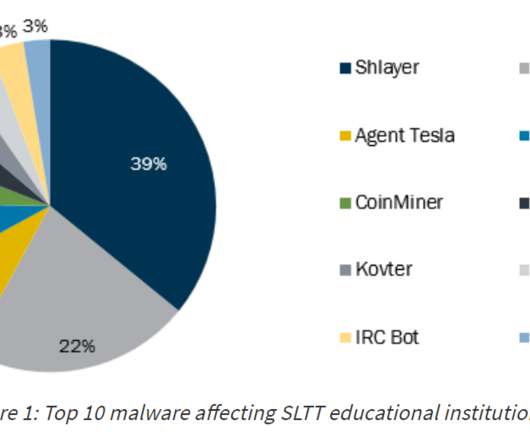




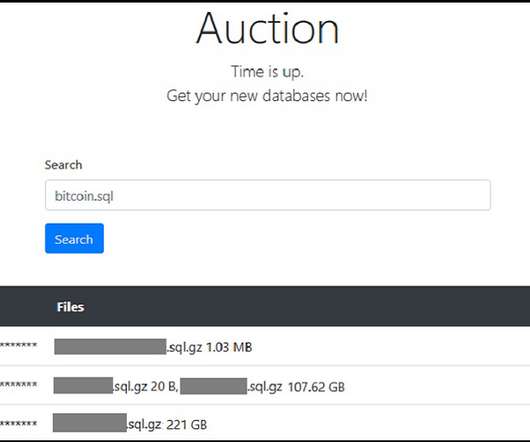





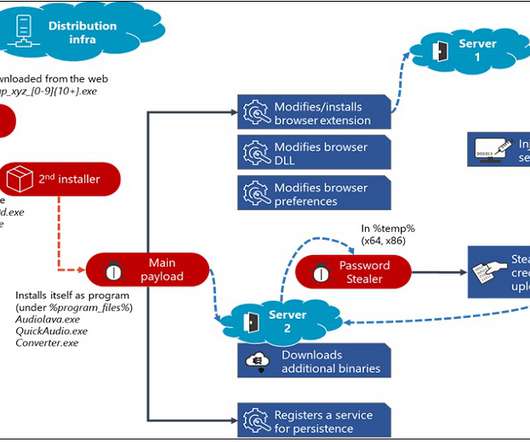

























Let's personalize your content