California EDD Prepaid Debit Card SMISHING Scam
This morning I received a text message informing me that my California EDD Prepaid Debit Card was being suspended with a deposit of $6,390 until I verified my Bank of America credit card:
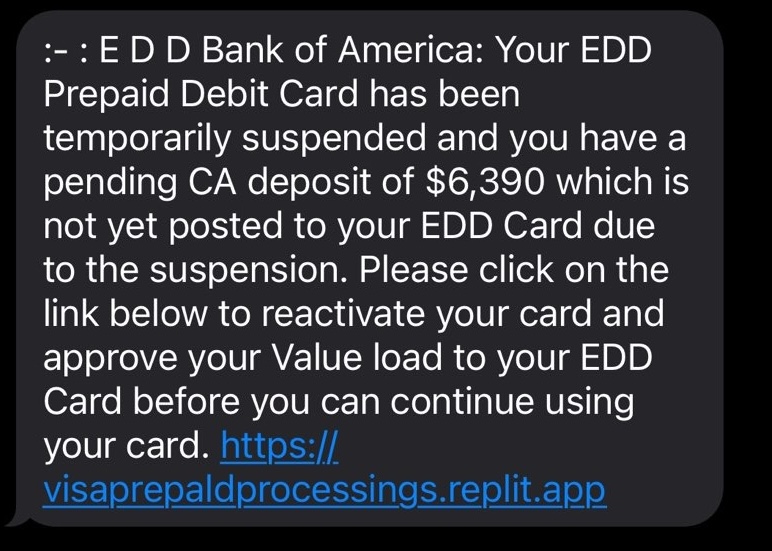
If you don’t live in California, this screams scam; but if you live in California and work with the CA EDD this could trick you into believing it is real.
Scams Capitalize on Real Events
In this scam bad actors are abusing a change being implemented by the California Employment Development Department (EDD), where they announced a switch to electronic benefit payments.
The transition from Bank of America to Money Network will begin with issuing new, enhanced prepaid debit cards with microchips, followed by providing a new direct deposit option later in the new year. Starting Monday, December 4, 2023, the EDD will send letters to about 850,000 Californians with active benefit claims informing them of key transition dates and actions.
Ca.gov EDD
This is further complicated becuase on January 17 2024 they also announced to expect notifications:
The Employment Development Department (EDD) is contacting unemployment, disability, and Paid Family Leave customers with timelines and information to assist in the transition from Bank of America debit cards to Money Network prepaid debit cards.
Ca.gov EDD
Knowing that they are switching from Bank of America to Money Network is important and will make sense when we look at the TTPs they employ:
How Scammers Siphon and Steal Information
The scammers take advantage of a real event and try to mirror information that is publicly accessible. They leverage a SMISHING campaign to target as many users as possible. Below I’ll break down how it works.
Scam Domains to Monitor and Blacklist
Here is what they did with the domains:
| https://www.visaprepaidprocessing.com/eddcard/Home/Index | Real site |
| visaprepaldprocessings.replit.app | Fake site – notice that they followed the similar nomenclature Notice that they misspelled. “paid” with an “l” instead of an “i” Notice that they are using the replit.app service to quickly spin up pages. |
Here is the anatomy of the scam and how it navigates between different systems to complete the cycle and capture as much information from the user as possible:

The main domain stealing information was ca-boaprepaidd.com and it seems to be registered, and likely hosted by Squarespace and proxied through CloudFlare:
Domain Name: ca-boaprepaidedd.com
Registry Domain ID: 2847513184_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.squarespace.domains
Registrar URL: https://domains2.squarespace.com
Updated Date: 2024-01-19T00:10:07Z
Creation Date: 2024-01-18T23:35:09Z
Registrar Registration Expiration Date: 2025-01-18T23:35:09Z
Registrar: Squarespace Domains II LLC
Registrar IANA ID: 895
Registrar Abuse Contact Email: abuse-complaints@squarespace.com
Registrar Abuse Contact Phone: +1.646-693-5324They also use both the replit.com app to quickly create the first redirect, and cognitoforms.com to upload information from the user.
What Users Experience In this Flow
When you open the website the scammers sent, this is what you will see:

The only thing that works on the page is the “continue” button. If you click on any of the other links you’ll see they are dead links. They even have validation to ensure you complete the form before proceeding.

After completing the form, they redirect you to a log in page, and even warn you that the log in might be different than what you typically use for Bank of America:

It looks like they accept whatever username and password you provide them. You should assume that if you enter the real username and password they are likely saving that information as well.
When you hit continue it takes you to a page to upload your ID:

Once you upload your information they complete the cycle by asking you to verify your information:

I tried calling the number, but the person I’m trying to reach does not have a voicemail that has been set up yet. HAHA
Be Weary of SMISHING Attacks
SMS-based Phishing Scams (SMISHING) has grown in popularity over the years because of its effectiveness against the general population. With text based attacks bad actors can take advantage of a users’ decision-making ability by focusing on things that are urgent, dangerous or personal as seen in the example above.
They will almost always look to abuse one, if not all, three of the following:
| Trust | By posing as a legitimate organization or person, attackers can lower their target’s skepticism. |
| Emotion | Attackers exploit users by driving panic. |
| Context | Cyberattacks can easily gather a few pieces of information and use it as content in an SMS message to you, effectively building a disguise. |
Similar to my last post on Online Scams targeting desktops you can almost always narrow down the groups most effected by this to kids, parents, and the elderly; cohorts of users that are either naive or technically deficient as it pertains to online threats.
Regardless of the tools we have at our disposal, one of the most effective methods of combating this is awareness and education.
