Biden Promises Retaliation Unless Putin Stops Cyberattacks
Data Breach Today
JUNE 17, 2021
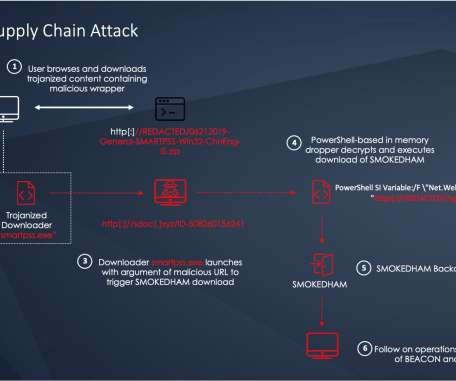
16 Critical Infrastructure Sectors Especially Off Limits - Or Else, President Warns U.S. President Joe Biden issued a clear warning to Russian President Vladimir Putin at their Geneva summit this week, saying that should Russia continue to launch cyberattacks against U.S. critical infrastructure sectors, or hack software supply chains, then Moscow should expect to see retaliation.






































Let's personalize your content