More than five years after domain name registrars started redacting personal data from all public domain registration records, the non-profit organization overseeing the domain industry has introduced a centralized online service designed to make it easier for researchers, law enforcement and others to request the information directly from registrars.

In May 2018, the Internet Corporation for Assigned Names and Numbers (ICANN) — the nonprofit entity that manages the global domain name system — instructed all registrars to redact the customer’s name, address, phone number and email from WHOIS, the system for querying databases that store the registered users of domain names and blocks of Internet address ranges.
ICANN made the policy change in response to the General Data Protection Regulation (GDPR), a law enacted by the European Parliament that requires companies to gain affirmative consent for any personal information they collect on people within the European Union. In the meantime, registrars were to continue collecting the data but not publish it, and ICANN promised it would develop a system that facilitates access to this information.
At the end of November 2023, ICANN launched the Registration Data Request Service (RDRS), which is designed as a one-stop shop to submit registration data requests to participating registrars. This video from ICANN walks through how the system works.
Accredited registrars don’t have to participate, but ICANN is asking all registrars to join and says participants can opt out or stop using it at any time. ICANN contends that the use of a standardized request form makes it easier for the correct information and supporting documents to be provided to evaluate a request.
ICANN says the RDRS doesn’t guarantee access to requested registration data, and that all communication and data disclosure between the registrars and requestors takes place outside of the system. The service can’t be used to request WHOIS data tied to country-code top level domains (CCTLDs), such as those ending in .de (Germany) or .nz (New Zealand), for example.
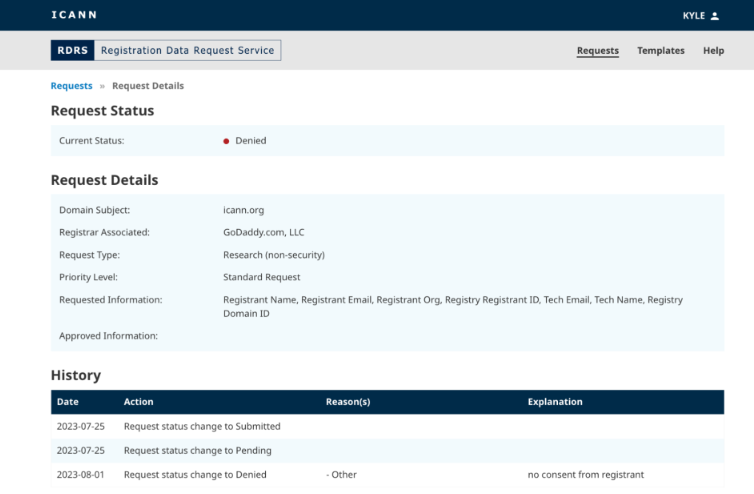
The RDRS portal.
As Catalin Cimpanu writes for Risky Business News, currently investigators can file legal requests or abuse reports with each individual registrar, but the idea behind the RDRS is to create a place where requests from “verified” parties can be honored faster and with a higher degree of trust.
The registrar community generally views public WHOIS data as a nuisance issue for their domain customers and an unwelcome cost-center. Privacy advocates maintain that cybercriminals don’t provide their real information in registration records anyway, and that requiring WHOIS data to be public simply causes domain registrants to be pestered by spammers, scammers and stalkers.
Meanwhile, security experts argue that even in cases where online abusers provide intentionally misleading or false information in WHOIS records, that information is still extremely useful in mapping the extent of their malware, phishing and scamming operations. What’s more, the overwhelming majority of phishing is performed with the help of compromised domains, and the primary method for cleaning up those compromises is using WHOIS data to contact the victim and/or their hosting provider.
Anyone looking for copious examples of both need only to search this Web site for the term “WHOIS,” which yields dozens of stories and investigations that simply would not have been possible without the data available in the global WHOIS records.
KrebsOnSecurity remains doubtful that participating registrars will be any more likely to share WHOIS data with researchers just because the request comes through ICANN. But I look forward to being wrong on this one, and will certainly mention it in my reporting if the RDRS proves useful.
Regardless of whether the RDRS succeeds or fails, there is another European law that takes effect in 2024 which is likely to place additional pressure on registrars to respond to legitimate WHOIS data requests. The new Network and Information Security Directive (NIS2), which EU member states have until October 2024 to implement, requires registrars to keep much more accurate WHOIS records, and to respond within as little as 24 hours to WHOIS data requests tied everything from phishing, malware and spam to copyright and brand enforcement.




It would be nice to have a list of registrars who opt out of this “service.”
Hey Greg. I’m actually working on a list of participants now. It’s a bit of a manual process. Stay tuned!
It looks like there are 56 entities currently working with the RDRS. While there are hundreds of domain registrars, some of the top registrars are participating (for the time being), including GoDaddy, eNom, Gandi, Namecheap and Network Solutions.
123-Reg Limited
Access Japan Co, Ltd․ dba REGne (www․regne․net)
Amazon Registrar, Inc․
Arcanes Technologies
Ascio Technologies, Inc․ Danmark – Filial af Ascio technologies, Inc․ USA
Blacknight Internet Solutions Ltd․
Blue Razor Domains, LLC
Bombora Technologies Pty Ltd
COREhub, S․R․L․
Corporation Service Company (DBS), Inc․
CORPORATION SERVICE COMPANY (UK) LIMITED
Cross Marketing Technology Ltd․
CSC Corporate Domains, Inc․
CSC Management Consulting (Shanghai) Co․, Ltd․
Deutsche Telekom AG
eNom, LLC
EPAG Domainservices GmbH
Focus IP, Inc․ dba Tracer
Gandi SAS
Go Australia Domains, LLC
Go Canada Domains, LLC
Go China Domains, LLC
Go France Domains, LLC
Go Montenegro Domains, LLC
GoDaddy Corporate Domains, LLC
GoDaddy Online Services Cayman Islands Ltd․
GoDaddy․com, LLC
Hongkong Kouming International Limited
Hosting Concepts B․V․ d/b/a Registrar․eu
Ilait AB
IP Twins SAS
Ledl․net GmbH
Lexsynergy Limited
Mesh Digital Limited
Name SRS AB
NameCheap, Inc․
NameWeb BVBA
Net-Chinese Co․, Ltd․
Network Solutions, LLC
Netzadresse․at Domain Service GmbH
Nom-iq Ltd․ dba COM LAUDE
Paragon Internet Group Ltd t/a Paragon Names
Porkbun LLC
Realtime Register B․V․
RegistrarBrand, LLC
RegistrarGuard, LLC
RegistrarSecure, LLC
RegistrarTrust, LLC
SafeBrands SAS
Shinjiru Technology Sdn Bhd
Spaceship, Inc․
Stichting Registrar of Last Resort Foundation
Tucows Domains Inc․
Webnames․ca Inc․
WHC Online Solutions Inc․
Wild West Domains, LLC
If participants can opt out or stop responding at any time, how will you know if this list is accurate and up-to-date? Is there any mechanism to keep an organization from saying, “Sure, we’ll respond to request” but actually failing to do so?
As you say, there is responding is a “cost center” so they have incentive not to respond. At least until NIS2 is implemented.
I did something similar last week.
https://domainincite.com/29238-most-registrars-are-shunning-icanns-new-whois-system
That’s great Brian and thanks for doing that but I wasn’t expecting you to do that legwork when I made my comment. 🙂
As the individual who worked at the Legal & Abuse Dept. of ICANN-accredited registrar I can tell you one thing: WHOIS data against court order. There simply is no other way.
I’ve owned an ORG domain for about 15 years. I’ve known how to use WHOIS all along. It was always a “superuser” privilege. I understood this “privilege” for what it was — a shady scam to promote demotion. The real problem is that people get full of themselves, and this “expertise” misdirects navigation. For example, the International Red Cross and the International Red Crescent are exactly the same domain.
“The problem in America isn’t so much what people don’t know; the problem is what people think they know that just ain’t so.” — Will Rogers
Aren’t the Red Cross and the Red Crescent the same organisation? There’s no way that a Muslim country will have anything to do with a “cross”, with its xtian connotations…
Since when was WHOIS a “superuser” privilege? Or running a domain for that matter? And the Red Cross and the Red Crescent are pretty much the same organisation, depending upon the official religion of that country.
Sorry but what does that mean ” WHOIS data against court order”?
It means you give us court order, we give you domain registrant / admin / tech contacts, if they are hidden behind whois privacy.
This is good for government agencies like the FBI, but this is tough for the independent security researcher community.
Fully agree with that, however the independent researcher community also has some shady freaks “with a (not less shady) mission”. So, if the requesting party has enough evidence to prove that the it’s the domain registrant (and not some other individual or organization) who’s engaged in unlawful or even criminal conduct, it should be easy to prove this in the court and get an order.
As a side note: to nullroute a domain takes *a lot* less effort than to get sensitive information.
Thanks!
Good info.
You are totally right that registrars and registries will be no more likely to answer if the request comes thru ICANN RDRS, but also no less likely. What they do is to perform a balancing test, as foreseen in privacy regulations, and disclose the information or not. Regardless of the request channel… what RDRS provides though is clear instructions to requesters to what information is required. This increases actionable information on the request, and that is something that adds to a better response rate.
I use whois extensively along with geoiplookup and dig, trying to interpret where fun Apache access log entries come from. Most of the times it is useless when trying to truly identify whom owns the given domain on lets say, a cloud provider, that is probing your site. The information many times is masked or just plain false. Sometimes, though, whois gives you actionable information, isolating a domain of interest down to an easily digestible CIDR 24 address space, along with accurate address information. In these cases, that good addressing information in conjunction with a graphical mapping application, allows for things like: “Wow, look who’s embassy is right next to the cafe that I am being probed from…”
BTW, a little OPSEC SOP is never use domain search tools from your administrative IP address, i.e. your house, when doing research. Always VPN to a place as close as possible to the domain of interest and operate from there.
A much better tool, IMHO, would be something that tells you every domain hosted on a given IP address. That would be priceless.
That tool exists my friend
Or I’ll rephrase: many exist — obviously mostly via paid, subscription model services by some specific companies. Accessible via website lookup etc just like all else
That’s a good step in this way scammed sites will be closed.
Can you provide examples of significant cybersecurity incidents or trends that KrebsOnSecurity has reported on, and how has the platform impacted the broader cybersecurity community?
Hey buddy, as Brian mentioned, just do a search against his site of ‘whois’ — many stories reported on where Brian uses various bits of Intel, and many or all include whois data in that hunt.. even with the data being fake, you’d be surprised how much he’s undercovered using just that bit of info.
Lowering the cost of obtaining such personal information such as your home address, phone number, email address, and name, to less than a warrant from a judge is dangerous.
The abuse that will ensue I bet will be far greater than abuse this policy change purports to (try to) stop.
Didn’t GoDaddy get caught being fast and loose with customer data?
Slimy registrars probably have on-site taxpayer-paid cyber cops making direct and unredacted queries; or merely providing an API for “good guys” to use while registrars exercise zero oversight for the purposes and lawfulness of the request. Or perhaps the registrars just “push” every new registration to $ubscrib€rs. It’s just a cash cow to them. Selling out customers is old hat.
People deserve freedom of speech. Upset people should focus on the content of the speech. Providing such easy access to this information grossly LOWERS THE BAR FOR BAD ACTORS who would otherwise NOT be able to carry out HARMFUL INTENT.
* People deserve to share their thoughts and media on their own website.
* They should not be forced to do it through “social media.”
* They should be able to put up password/etcetera barriers to restrict access to people they allow into that portion of their site.
* If they don’t wish to share such personal information as their country, state, street name and number, phone number, email address, or name , it should only be provided via a legal warrant.
My guess is Mr. Krebs may have a public facing phone #, email address, and PO box. But my guess is Brian also has some personal email addresses, phone number, and street address. And he prefers to keep that info as private as possible. [See](https://krebsonsecurity.com/2023/11/id-theft-service-resold-access-to-usinfosearch-data/) (BTW, I didn’t go searching for it an none of this should be construed to be a threat from me to Brian.)
But not all of us can afford to pay for PO boxes, multiple phones, an intermediary to handle requests, etcetera.
Again, the abuse that will ensue I bet will be far greater than abuse this policy change purports to (try to) stop.
1) get a legal warrant.
2) stop selling your customers data.
The ICANN video has been removed I believe
I received this response from Porkbun support after inquiring about their participation in RDRS:
—-
I understand your concern but in this regard we, and many others, are only participating insomuch that we are able to comment on and influence policy. Participation in no way means that a participating registrar will disclose data to a third party. There also seems to be a misunderstanding of what RDRS is, the purpose of RDRS is only to streamline requests and does not affect actual disclosure. Customer very privacy is important to us and we would never voluntarily participate in any program that would jeopardize privacy in any way. Any request for data via RDRS is treated no different than a request being made via email/postal mail/etc, the request still has to be processed on our side through normal channels and meet the strict legal criteria required for any sort of disclosure.
You can find more information here: https://www.icann.org/rdrs-en A very important clause on that page is:
“Important note: The Registration Data Request Service will not guarantee access to the registration data. All communication and data disclosure between the registrars and requestors will take place outside of the system.”
The situation at ICANN is getting worse. The WHOIS “disclosure” system that ICANN just rolled out is a joke and a delaying tactic by the contracted parties that will not solve the problem and thus will continue to put US cybersecurity, consumer privacy, and child protection at risk. In fact, for accuracy, it was renamed to “WHOIS Request System.”
The WHOIS Request system is voluntary, only applies to the registrars, not the registries like Verisign that manages .com, and has no data accuracy requirements. Since there is no mandate for an ICANN contracted party to “disclose” data or even participate in the request system, this system is the current status quo.
So, to predict the outcome, the data will show that this “Request” ticketing system will not be utilized, thus allowing ICANN and the contracted parties to argue that there is no real interest in WHOIS data. In the meantime, after 5 years of ICANN trying to fix the Dark WHOIS problem and an additional two years with this system, US cybersecurity and consumer/child protection will continue to be at greater risk.