Phishing campaign targets LATAM e-commerce users with Chaes Malware
Security Affairs
NOVEMBER 18, 2020
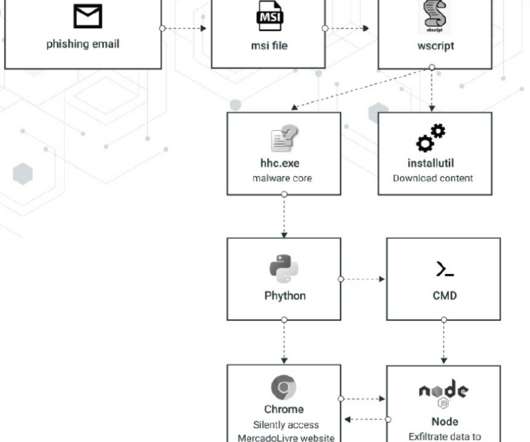
bin, researchers also observed the use of a cryptocurrency mining module. . The attackers use Microsoft Word’s built-in feature to fetch a payload from a remote server, by changing the template target of the settings.xml file which is embedded in the document and populating this field with a download URL of the next payload.






























Let's personalize your content