ADVERSARIAL OCTOPUS – ATTACK DEMO FOR AI-DRIVEN FACIAL RECOGNITION ENGINE
Security Affairs
JUNE 22, 2021
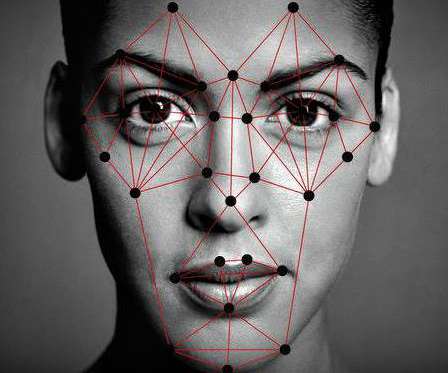
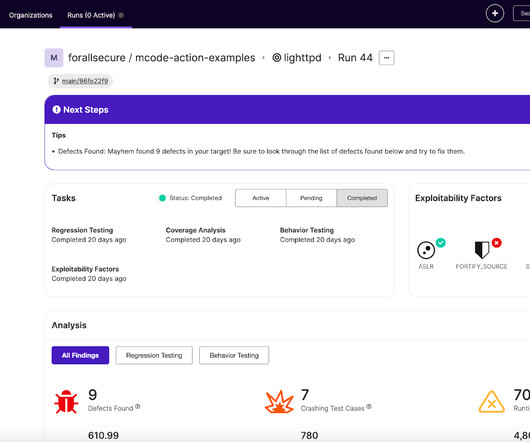
ATTACK DEMO. We present an example of how PimEyes.com, the most popular search engine for public images and similar to Clearview, a commercial facial recognition database sold to law enforcement and governments, has mistaken a man for Elon Musk in the photo. Original post at: Face Recognition Attack Demo: Adversarial Octopus.











































Let's personalize your content