FBI to Share Compromised Passwords With Have I Been Pwned
Data Breach Today
MAY 28, 2021
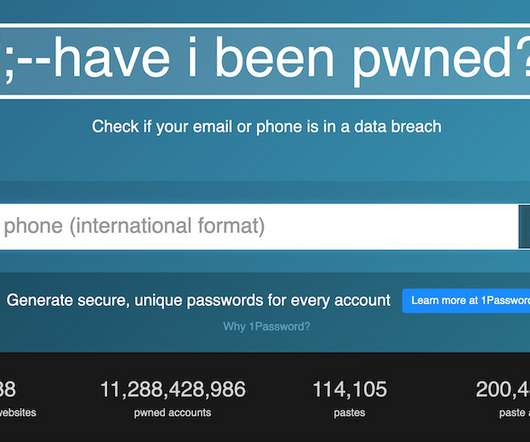
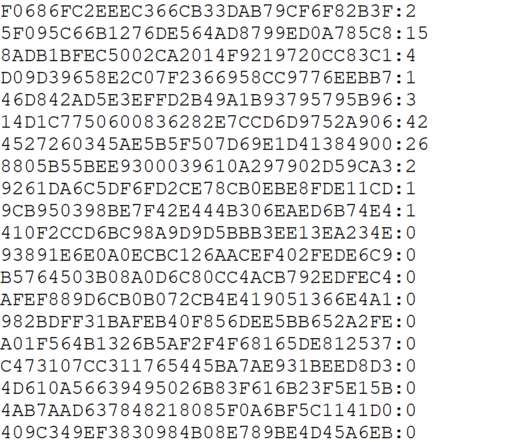
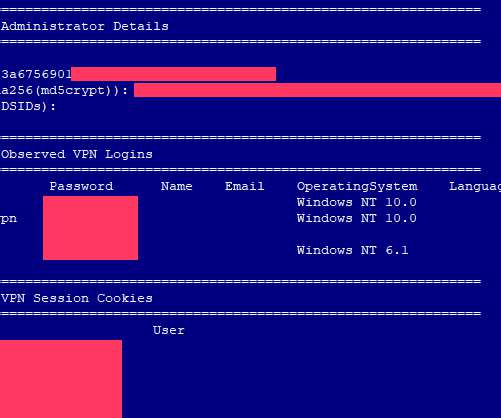
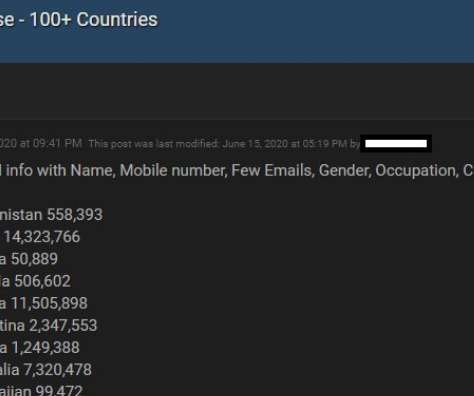
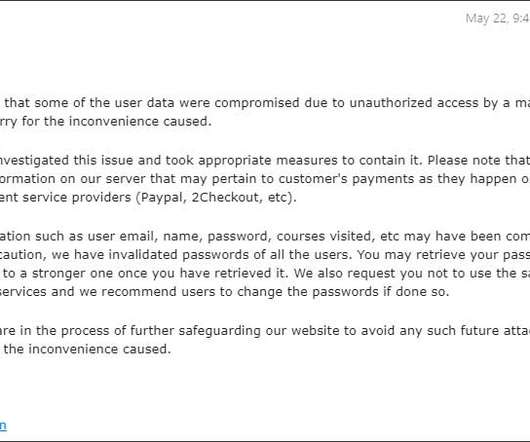
Will Help Prevent Users From Reusing Risky Passwords The FBI will soon begin sharing hashes of compromised passwords found in the course of its cybercrime investigations with Have I Been Pwned, a data breach notification service.








































Let's personalize your content