NEW TECH: DigiCert Document Signing Manager leverages PKI to advance electronic signatures
The Last Watchdog
JULY 21, 2021
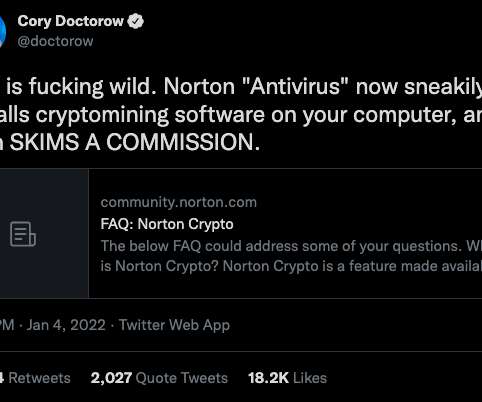
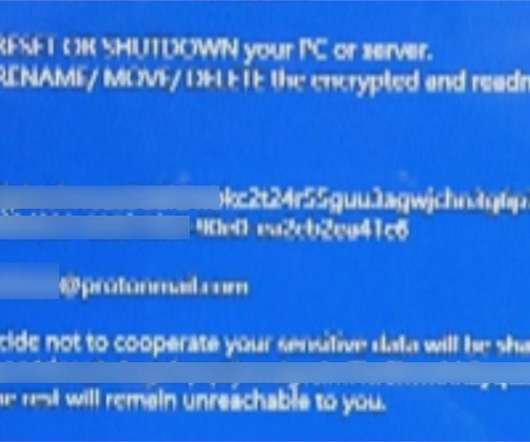
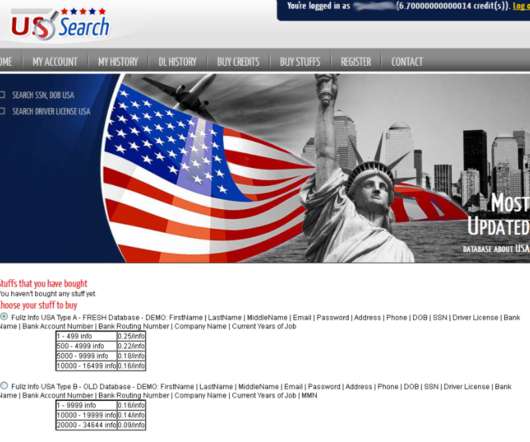
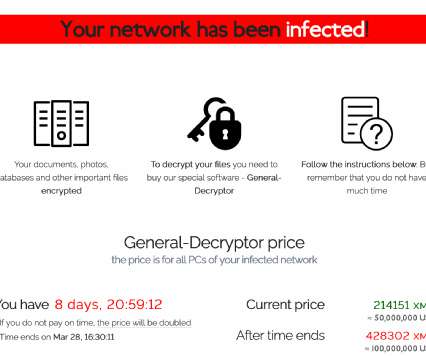
Most of us, by now, take electronic signatures for granted. Yet electronic signatures do have their security limitations. As digital transformation has quickened, it has become clear that electronic signatures are destined to become even more pervasively used to conduct business remotely. Achieving high assurance.









































Let's personalize your content