PCI DSS 4.0: The Compliance Countdown – A Roadmap Through Phases 1 & 2
Thales Cloud Protection & Licensing
APRIL 10, 2024
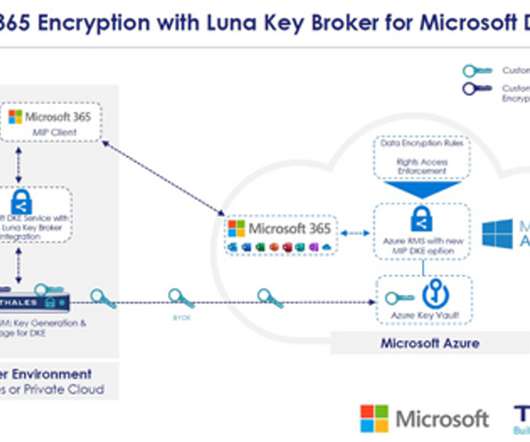
The Compliance Countdown – A Roadmap Through Phases 1 & 2 madhav Thu, 04/11/2024 - 05:17 While compliance mandates can sometimes feel burdensome, PCI DSS 4.0 strategy can lay a foundation for compliance with other data protection frameworks like DORA, NIS2, and the GLBA. Harmonizing Compliance: Aligning PCI DSS 4.0


















































Let's personalize your content