While the cybersecurity world is focused on the Russian invasion of Ukraine, new research from Symantec serves as a reminder that significant threats remain elsewhere too.
Symantec this week reported a highly sophisticated malware called “Backdoor.Daxin” that “appears to be used in a long-running espionage campaign against select governments and other critical infrastructure targets” and appears to be linked to China.
The researchers called Daxin “a highly sophisticated piece of malware being used by China-linked threat actors, exhibiting technical complexity previously unseen by such actors. The malware appears to be used in a long-running espionage campaign against select governments and other critical infrastructure targets.”
Symantec said the backdoor’s purpose is to exfiltrate data stealthily and can remain undetected even by networks with high defense capabilities. Symantec’s team said the threat will probably require further in-depth analyses to uncover all the details.
“Daxin is without doubt the most advanced piece of malware Symantec researchers have seen used by a China-linked actor,” the researchers wrote. “Considering its capabilities and the nature of its deployed attacks, Daxin appears to be optimized for use against hardened targets, allowing the attackers to burrow deep into a target’s network and exfiltrate data without raising suspicions.”
Also read: SANS Outlines Critical Infrastructure Security Steps as Russia, U.S. Trade Cyberthreats
Daxin’s Impressive Ability to Remain Undetected
Technically speaking, Daxin is a backdoor installed as a Windows kernel driver, which is a pretty unusual format for malware. The attackers use it to conduct various unauthorized operations on target machines, such as exfiltrating confidential documents or sending malicious payloads.
So far, nothing new. However, Symantec researchers concluded Daxin is particularly stealthy, with a powerful ability to communicate over hijacked TCP/IP connections. It swaps legitimate connections with encrypted channels to bypass firewall rules and evade most detection tools like EDR.
The malware then sends information back to remote servers. This point seems to be the key to understanding this unusual backdoor: The malware does not create any additional network processes that can set off alerts, but rather attacks legitimate services already running.
To proceed, it monitors specific patterns in incoming TCP traffic and then attempts to disconnect a legitimate recipient to take its place. If the exchange is successful, that channel will be used to receive command-and-control instructions and exfiltrate data.
Also read: Best Network Monitoring Tools
Multi-node Communications a New Tactic
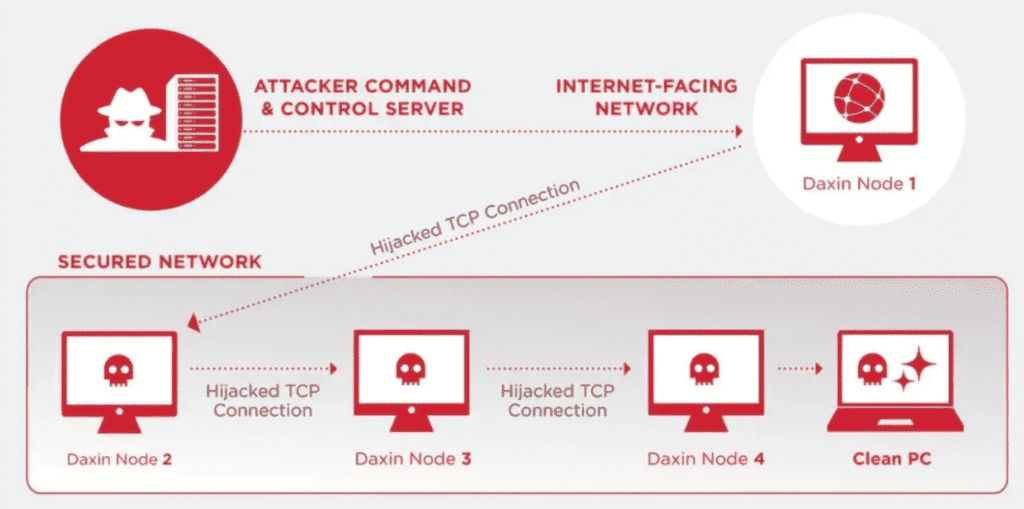
Symantec included a graphic (see below) to explain how Daxin can sneak into secure environments by establishing multi-node communication channels with a new approach. The attackers can manipulate multiple infected computers in a single operation, while most similar attacks would use a step-by-step approach that would require separate operations.
This approach may significantly lower the chance of detection, according to Symantec:
The multi-node architecture makes it possible to compromise computers recursively by relaying commands across the network and hiding communication channels deeply, which also extends the dwell period for malicious activities.
Researchers published a detailed list of the potential resources used in Daxin attacks, for example, using filenames such as “patrol.sys”, “wantd.sys”, or backdoors such as 514d389ce87481fe1fc6549a090acf0da013b897e282ff2ef26f783bd5355a01.
See the Top Endpoint Detection & Response (EDR) Solutions
Codebase Dates to 2009
While the latest sample was discovered in November 2021, Symantec believes the malware contains blocks of instructions that recall Regin, an advanced espionage tool discovered by Symantec threat researchers in 2014. They also connected it to Zala, an older piece of malware discovered in 2009 that could have been the first experiments that led to Daxin many years later.
Symantec’s team found significant similarities in codebases that indicate it’s probably the same actor or, at least, a group that “had access to Zala’s codebase.”
There is no clear evidence of a single actor for now, but according to Symantec, the attack “appears to be organizations and governments of strategic interest to China,” as “tools associated with Chinese espionage actors were found on some of the same computers where Daxin was deployed.”
In any case, the new threat does not look like the traditional analytics collected during China-related attacks, which might put the threat on a whole new level.
Symantec collaborated with the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to warn foreign governments and help victims. CISA urged organizations to review Symantec’s report “for more information and for a list of indicators of compromise that may aid in the detection of this activity.”
This could be the latest chapter in the perpetual cyberwar between the U.S. and China, following recent claims by Chinese firms that the NSA hacked their infrastructure. Chinese researchers disclosed details about an advanced persistent threat (APT) called “bvp47,” named after an encryption algorithm attributed to the NSA.
Read next: Top Vulnerability Management Tools