Case Study: A REvil Ransom Negotiation
Data Breach Today
JULY 20, 2021
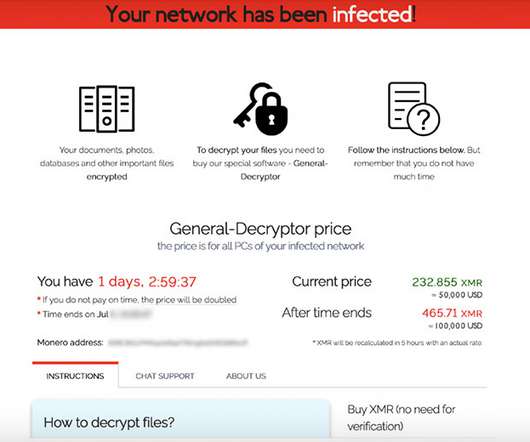
Security Firm Elliptic Illustrates How Group Was Willing to Reduce Its Demands The blockchain analysis firm Elliptic offers a step-by-step case study, based on its research, of how one victim of the REvil ransomware gang negotiated a lower ransom payment.
















































Let's personalize your content