If you’ve ever owned a domain name, the chances are good that at some point you’ve received a snail mail letter which appears to be a bill for a domain or website-related services. In reality, these misleading missives try to trick people into paying for useless services they never ordered, don’t need, and probably will never receive. Here’s a look at the most recent incarnation of this scam — DomainNetworks — and some clues about who may be behind it.
The DomainNetworks mailer may reference a domain that is or was at one point registered to your name and address. Although the letter includes the words “marketing services” in the upper right corner, the rest of the missive is deceptively designed to look like a bill for services already rendered.
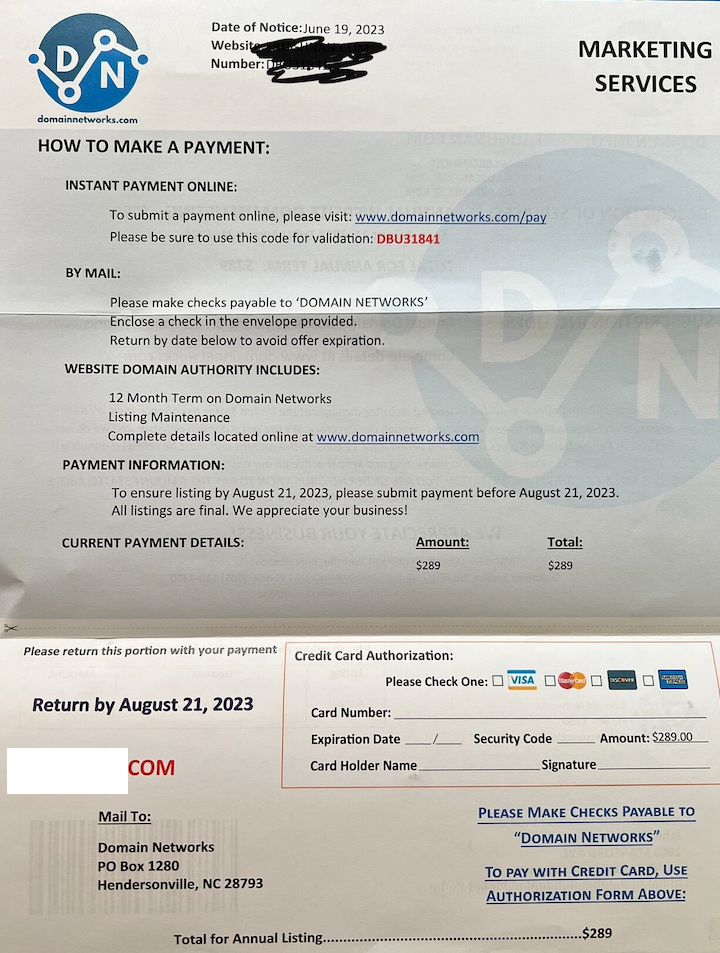
DomainNetworks claims that listing your domain with their promotion services will result in increased traffic to your site. This is a dubious claim for a company that appears to be a complete fabrication, as we’ll see in a moment. But happily, the proprietors of this enterprise were not so difficult to track down.
The website Domainnetworks[.]com says it is a business with a post office box in Hendersonville, N.C., and another address in Santa Fe, N.M. There are a few random, non-technology businesses tied to the phone number listed for the Hendersonville address, and the New Mexico address was used by several no-name web hosting companies.
However, there is little connected to these addresses and phone numbers that get us any closer to finding out who’s running Domainnetworks[.]com. And neither entity appears to be an active, official company in their supposed state of residence, at least according to each state’s Secretary of State database.
The Better Business Bureau listing for DomainNetworks gives it an “F” rating, and includes more than 100 reviews by people angry at receiving one of these scams via snail mail. Helpfully, the BBB says DomainNetworks previously operated under a different name: US Domain Authority LLC.
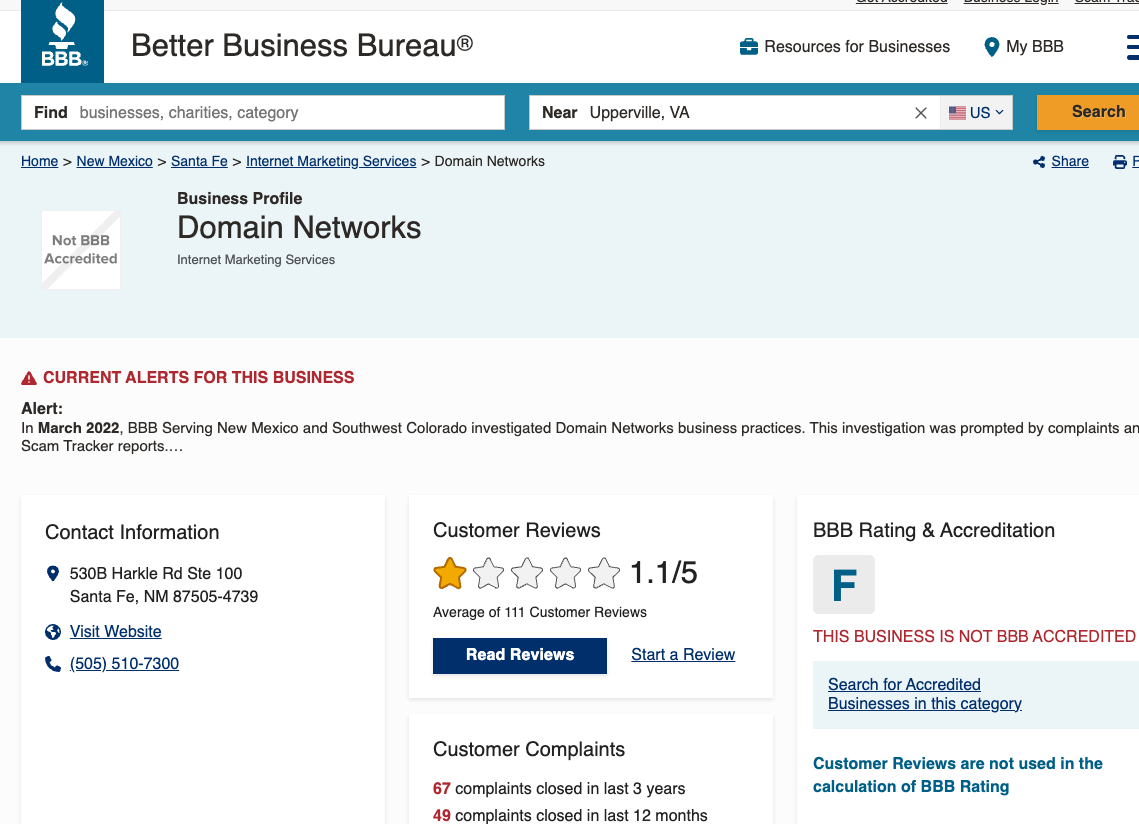
DomainNetworks has an “F” reputation with the Better Business Bureau.
Copies of snail mail scam letters from US Domain Authority posted online show that this entity used the domain usdomainauthority[.]com, registered in May 2022. The Usdomainauthority mailer also featured a Henderson, NC address, albeit at a different post office box.
Usdomainauthority[.]com is no longer online, and the site seems to have blocked its pages from being indexed by the Wayback Machine at archive.org. But searching on a long snippet of text from DomainNetworks[.]com about refund requests shows that this text was found on just one other active website, according to publicwww.com, a service that indexes the HTML code of existing websites and makes it searchable.
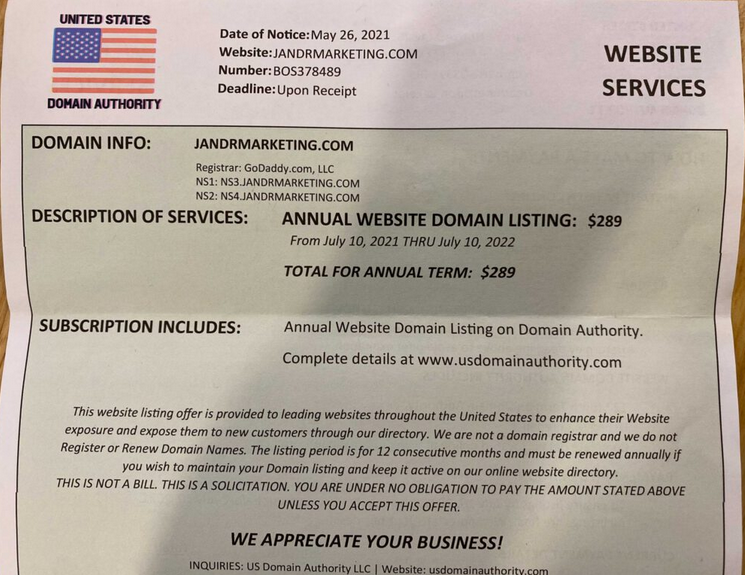
A deceptive snail mail solicitation from DomainNetwork’s previous iteration — US Domain Authority. Image: Joerussori.com
That other website is a domain registered in January 2023 called thedomainsvault[.]com, and its registration details are likewise hidden behind privacy services. Thedomainsvault’s “Frequently Asked Questions” page is quite similar to the one on the DomainNetworks website; both begin with the question of why the company is sending a mailer that looks like a bill for domain services.
Thedomainsvault[.]com includes no useful information about the entity or people who operate it; clicking the “Contact-us” link on the site brings up a page with placeholder Lorem Ipsum text, a contact form, and a phone number of 123456789.
However, searching passive DNS records at DomainTools.com for thedomainsvault[.]com shows that at some point whoever owns the domain instructed incoming email to be sent to ubsagency@gmail.com.
The first result that currently pops up when searching for “ubsagency” in Google is ubsagency[.]com, which says it belongs to a Las Vegas-based Search Engine Optimization (SEO) and digital marketing concern generically named both United Business Service and United Business Services. UBSagency’s website is hosted at the same Ann Arbor, Mich. based hosting firm (A2 Hosting Inc) as thedomainsvault[.]com.
UBSagency’s LinkedIn page says the company has offices in Vegas, Half Moon Bay, Calif., and Renton, Wash. But once again, none of the addresses listed for these offices reveal any obvious clues about who runs UBSagency. And once again, none of these entities appear to exist as official businesses in their claimed state of residence.
Searching on ubsagency@gmail.com in Constella Intelligence shows the address was used sometime before February 2019 to create an account under the name “Sammy\Sam_Alon” at the interior decorating site Houzz.com. In January 2019, Houzz acknowledged that a data breach exposed account information on an undisclosed number of customers, including user IDs, one-way encrypted passwords, IP addresses, city and ZIP codes, as well as Facebook information.
Sammy\Sam_Alon registered at Houzz using an Internet address in Huntsville, Ala. (68.35.149.206). Constella says this address was associated with the email tropicglobal@gmail.com, which also is tied to several other “Sammy” accounts at different stores online.
Constella also says a highly unique password re-used by tropicglobal@gmail.com across numerous sites was used in connection with just a few other email accounts, including shenhavgroup@gmail.com, and distributorinvoice@mail.com.
The shenhavgroup@gmail.com address was used to register a Twitter account for a Sam Orit Alon in 2013, whose account says they are affiliated with the Shenhav Group. According to DomainTools, shenhavgroup@gmail.com was responsible for registering roughly two dozen domains, including the now-defunct unitedbusinessservice[.]com.
Constella further finds that the address distributorinvoice@mail.com was used to register an account at whmcs.com, a web hosting platform that suffered a breach of its user database several years back. The name on the WHMCS account was Shmuel Orit Alon, from Kidron, Israel.
UBSagency also has a Facebook page, or maybe “had” is the operative word because someone appears to have defaced it. Loading the Facebook page for UBSagency shows several of the images have been overlaid or replaced with a message from someone who is really disappointed with Sam Alon.
“Sam Alon is a LIAR, THIEF, COWARD AND HAS A VERY SMALL D*CK,” reads one of the messages:

The current Facebook profile page for UBSagency includes a logo that is similar to the DomainNetworks logo.
The logo in the UBSagency profile photo includes a graphic of what appears to be a magnifying glass with a line that zig-zags through bullet points inside and outside the circle, a unique pattern that is remarkably similar to the logo for DomainNetworks:

The logos for DomainNetworks (left) and UBSagency.
Constella also found that the same Huntsville IP address used by Sam Alon at Houzz was associated with yet another Houzz account, this one for someone named “Eliran.”
The UBSagency Facebook page features several messages from an Eliran “Dani” Benz, who is referred to by commenters as an employee or partner with UBSagency. The last check-in on Benz’s profile is from a beach at Rishon Letziyon in Israel earlier this year.
Neither Mr. Alon nor Mr. Benz responded to multiple requests for comment.
It may be difficult to believe that anyone would pay an invoice for a domain name or SEO service they never ordered. However, there is plenty of evidence that these phony bills often get processed by administrative personnel at organizations that end up paying the requested amount because they assume it was owed for some services already provided.
In 2018, KrebsOnSecurity published How Internet Savvy are Your Leaders?, which examined public records to show that dozens of cities, towns, school districts and even political campaigns across the United States got snookered into paying these scam domain invoices from a similar scam company called WebListings Inc.
In 2020, KrebsOnSecurity featured a deep dive into who was likely behind the WebListings scam, which had been sending out these snail mail scam letters for over a decade. That investigation revealed the scam’s connection to a multi-level marketing operation run out of the U.K., and to two brothers living in Scotland.




Very similar to the scam invoices patent and trademark owners regularly receive.
Yup; they’re so common that major intellectual property offices maintain scam awareness web pages listing known scammers with examples of the official-looking stuff they send out (see examples below). IP practitioners routinely warn their clients to expect and ignore the scam notices / invoices, but the things keep coming because it’s easy to automate the process–the scammers just scrape the name & address information from the detailed records published by the IP Offices. Those records also contain date details, enabling scammers to time the arrival of their invoices to coincide with (or precede) the time when a legitimate invoice would be expected, e.g. for payment of a renewal fee to maintain a patent or trademark registration.
See:
https://www.uspto.gov/trademarks/protect/caution-misleading-notices
https://ised-isde.canada.ca/site/canadian-intellectual-property-office/en/warning-scam-notices-related-patents-or-trademarks
https://www.epo.org/news-events/news/2021/20210802.html
and so on.
Or, on the flip side, baseless and fabulistic DMCA notices are sent out like old school email spam, although that is very much a product of the law and how it was drafted instead of some unforeseen opportunity.
“chances are good” I can only confirm the odds. I never fell for third-party scam.
Sadly the first party cousin, sign-up with no hope of cancellation, is alive and well too.
Owners of US Coast Guard documented vessels receive similar scam mailings to renew the documentation.
I have gotten these from “Domain Registry of Canada”, as have my clients. Some of them are older people with domains I’ve set up for them because they’ve had issues with Telus/Shaw/Gmail/Hotmail etc mail systems and have gotten their own domains through providers like Webnames.ca. Because I’ve worked hard to establish a high level of trust with my clients, they call me when they get these, and I tell them to shred them….but they do get them. I think that some kind of harvesting is going on at some of the domain providers, and that contrary to their denials, (I’m looking at you, Telus!) hacks have happened that have exposed account names and passwords. A significant number of former Telus mail users have gotten sextortion emails with previously valid passwords as well. Scammers like Sammy flourish because of denials of large domain providers with crappy security and a stubborn lack of clarity about breaches.
My Canadian clients get these as well, but I can’t attribute it to weak security at any Canadian ISP (as much as I would like to). I registered these domains through Network Solutions or Tucows. This was before the availability of domain privacy services, and suspect that the scammers manually pulled registration info and put it into a database. I still receive domain email scams for domains that have expired over a decade ago.
Btw, it’s Rishon Letziyon, two words, not Rishon Le Siyon (three words). Just a small correction. It’s a city about 25 mins from Tel Aviv, not noteworthy in any way for technology.
Thanks!
Google maps calls it Rishon LeTsiyon
https://www.google.com/maps/place/Rishon+LeTsiyon,+Israel/@31.975175,34.7004481
Wikipedia calls it Rishon LeZion
https://en.wikipedia.org/wiki/Rishon_LeZion
Non-Latin alphabets seem to frequently cause transliteration ambiguities
Theres a few bigger datacenters there, as well as a fiber hub for 013/Netvision. Most telcos offer transit in the city as well.
I’ve been getting those for years…. Just adds to the bulk of my recycling bin…. Scammers will scam….
Birds gotta fly,
This stuff will last
Even after we die.
(Sorry, Oscar Hammerstein, Jr. RIP.
Yeah, I used to get that stuff for my personal domains, but now I’m behind a privacy service (bundled “free” with my registrations at my current registrar) so I don’t get it any more.
I know who my domains are registered with so I never fell for any of that crap, whether by snail mail or by email.
I used to help track down grifters that created fake scholarly journal publishing websites. This has all the same hallmarks, such as the laziness where they create similar sites and logos while reusing wording. Now, Americans generally don’t put US in a lot of business names unless there’s a specific need, or they’re trying to appeal to patriotic conservatives. A lot of overseas scammers seem to think adding US to their name makes them sound more like a legit American business. Rather funny. And those mailing addresses are most likely virtual forwarding addresses. Cool hat trick I learned? Several states almost always had all the scammy journal LLC registrations b/c you don’t even have to be a citizen, show up in person, or verify anything really to register. Or just use a company. Top state I always saw grifters register in? Delaware. And wouldn’t you know it? Domain Network Solutions LLC is registered in Delaware. Can’t tell it’s status w/o paying $10 though. It was formed 6/5/2013 (they used a third party company to register.) I assumed they had some active US business registration since those checks are made to the LLC. Would almost have to send them a check to see where it goes, but I’m not interested in making them more $$$ lol
“Americans generally don’t put US in a lot of business names unless there’s a specific need, or they’re trying to appeal to patriotic conservatives. A lot of overseas scammers seem to think adding US to their name makes them sound more like a legit American business.”
It’s amazing how much overlap there is between patriotic conservatives and overseas scammers lately.
I just want to know, what does the size of Sam Alon’s d*ck have to do with anything?
I get fake domain renewal scams in the mail annually from an outfit calling themselves Domain Registry of America, or a similar variation. They word the letters to look like they are my registrar and failure to renew will cause the domain to go offline. The renewal rate is about 6 times higher than what my actual Registrar charges. I can imagine that a busy company paymaster might fall for this scam and write a check because it takes time and effort to discover who their domains are registered with. The outfit operates out of a post office box in New Jersey.
I have been getting these for years and the cost is what usually triggers my attention as I know the general investment for my domain with the two providers you mentioned. It is very misleading!
I’ve received similar scams for renewal of my amateur radio license.
Thanks for all your sleuthing on this perennial scam. I hope the exposure not only raises awareness but serves as a deterrent for bottom dwellers thinking they can make a quick buck off less savvy domain owners/administrators.
Fantastic investigation, very interesting. Would the authorities have any interest in this kind of info? Note on that Eliran “Dani” Benz Facebook link that they have posted a review for a company called BS Consultants which they have said handles Google My Business listings for “their clients”, i.e. Eliran’s clients. Another avenue of enquiry?
Appreciate the legwork on this one, Brian. As a domain investor for nearly three decades I’ve been receiving these letters for about as long. But even if you find them, it is likely their operation is legal. Their small print usually states that signature and payment authorizes then to transfer the domain.* (*Not a lawyer) But I applaud any effort to expose this unethical practice, as it could lead to better laws preventing such tactics.