Enterprise IT, network and security product vulnerabilities were among those actively exploited in zero-day attacks last year, according to a recent Mandiant report.
Mandiant tracked 55 zero-day vulnerabilities that were actively exploited in 2022. That’s fewer than the 81 zero-days exploited in 2021, but far more than those exploited in any previous year. Going forward, Mandiant expects the trend for zero-day exploitation to continue to rise.
“A number of factors may have contributed to the zero-day count in 2020 dipping, then quadrupling in 2021,” researchers James Sadowski and Casey Charrier wrote. “Pandemic related disruptions in 2020 potentially interrupted reporting and disclosure workflows for vendors, reduced capacity for defenders to detect exploitation activity, and may have encouraged attackers to reserve novel exploits except in the most important cases.”
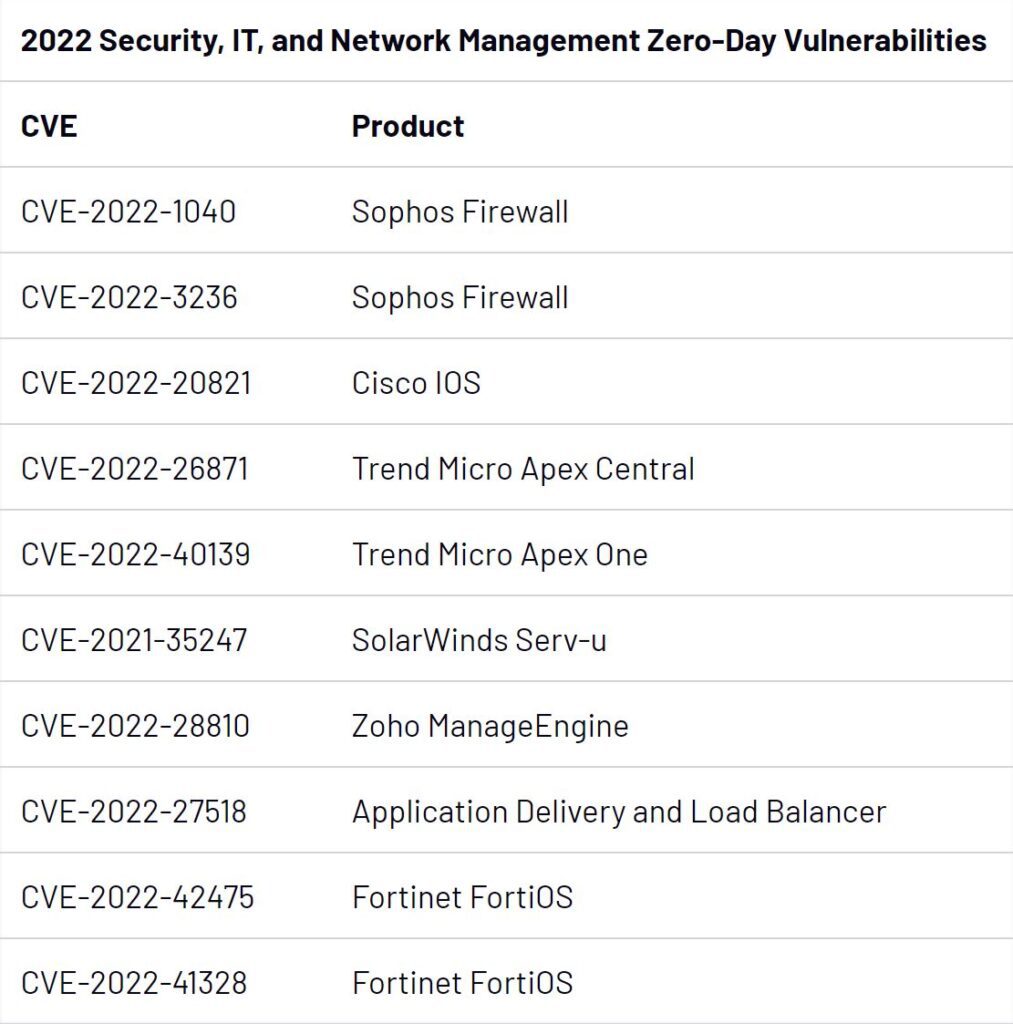
The most-exploited products, according to the report, were operating systems (19 zero-days); followed by browsers (11 zero-days); and security, IT, and network management products (10 zero-days).
State-sponsored Attacks Dominate
Mandiant identified a motive for 16 cases of zero-day exploitation. A quarter were financially motivated, and three of those were linked to ransomware operations. Overall, the proportion of financially motivated zero-day exploitation decreased in 2022.
Far more of the 16 cases with a clear motive were state-sponsored – 13 of the zero-days tracked in 2022 appear to have been leveraged by cyber espionage groups. At least half of those were linked to Chinese state-sponsored groups, and two appear to have been exploited by North Korean actors.
“Three campaigns in 2022 were particularly notable due to the involvement of multiple groups, expansive targeting, and focus on enterprise networking and security devices: multiple groups exploiting CVE-2022-30190 in early 2022, and the 2022 exploitation of FortiOS vulnerabilities CVE-2022-42475 and CVE-2022-41328,” the researchers observed.
Also read: Network Protection: How to Secure a Network
Follina State-Sponsored Campaigns
CVE-2022-30190, a.k.a. Follina, is a vulnerability in Microsoft Diagnostics Tool (MDST), exploited by persuading victims to open Word documents, which can enable the attacker to execute arbitrary code.
“We observed at least three separate activity sets exploit Follina as a zero-day in support of operations against public and private organizations in three distinct regions,” the researchers wrote. “Multiple separate campaigns may indicate that the zero-day was distributed to multiple suspected Chinese espionage clusters via a digital quartermaster.”
The three activity sets included a campaign against the Philippine government between March and May 2022; a campaign against telecommunications and business service providers in South Asia in April 2022; and a campaign against organizations in Belarus and Russia in May 2022.
Targeting Firewalls and IPS/IDS Appliances
In the case of CVE-2022-42475, a flaw in Fortinet’s FortiOS SSL-VPN, Mandiant observed a Chinese state-sponsored group exploiting the vulnerability in late 2022.
“This activity continues China’s pattern of exploiting internet-facing devices, especially those used for managed security purposes (e.g. firewalls, IPS/IDS appliances, etc.),” the researchers wrote. “We anticipate this tactic will continue to be the intrusion vector of choice for well-resourced Chinese groups.”
In mid-2022, Mandiant attributed exploitation of CVE-2022-41328 to the suspected Chinese cyber espionage group UNC3886. “With initial access to a publicly exposed FortiManager device, UNC3886 exploited a directory traversal zero-day vulnerability in FortiOS (CVE-2022-41328) to write files to FortiGate firewall disks outside of the normal bounds allowed with shell access,” the researchers wrote.
Exploitation of enterprise IT zero-day vulnerabilities are continuing into 2023, led by a Fortra GoAnywhere zero-day that has been behind more than a hundred attacks by the Clop ransomware group.
Commercial Use of Zero-Days
Mandiant also observed three cases in which commercial spyware companies leveraged zero-day flaws. “Despite recent struggles of some high-profile vendors, we assess with moderate confidence that there continues to be a very active and vibrant market for third-party malware, particularly surveillance tools, across the globe,” the researchers wrote.
The three companies, Candiru, Variston, and DSIRF, appear to have leveraged CVE-2022-2294 (targeting Google Chrome), CVE-2022-26485 (targeting Firefox), and CVE-2022-22047 (targeting Microsoft Windows Server) respectively.
“DSIRF’s zero-day exploit was reportedly leveraged to target law firms, banks, and strategic consultancies in countries including Austria, the United Kingdom, and Panama,” the researchers noted.
Vulnerabilities at the Network Edge
The report points to several factors that make security, network, and IT management products particularly attractive targets. “First, they are accessible to the internet, and if the attacker has an exploit, they can gain access to a network without requiring any victim interaction,” the researchers wrote. “This allows the attacker to control the timing of the operation and can decrease the chances of detection.”
Running malware on an internet-connected device can also enable lateral movement into the network and can be used to tunnel commands in and data out. “It is important to note that many of these types of products do not offer a simple mechanism to view which processes are running on the device’s operating systems,” the researchers added. “These products are often intended to inspect network traffic, searching for anomalies as well as signs of malicious behavior, but they are often not inherently protected themselves.”
How to Protect Your Organization
Looking ahead, the report anticipates that ongoing migration to cloud products could impact future trends regarding zero-days. Cloud vendors can manage and deploy patches for their customers, though Mandiant notes that some cloud vendors have failed in the past to disclose vulnerabilities in their own products.
In the meantime, Mandiant urges organizations to prioritize patching in order to mitigate risk.
“In addition to risk ratings, we suggest that organizations should analyze the following: types of actors targeting their specific geography or industry, common malware, frequent tactics, techniques, and procedures of malicious actors, and products used by an organization that provide the largest attack surfaces, all of which can inform resource allocation to mitigate risk,” the researchers advised.
Further reading:






