Ezuri memory loader used in Linux and Windows malware
Security Affairs
JANUARY 8, 2021
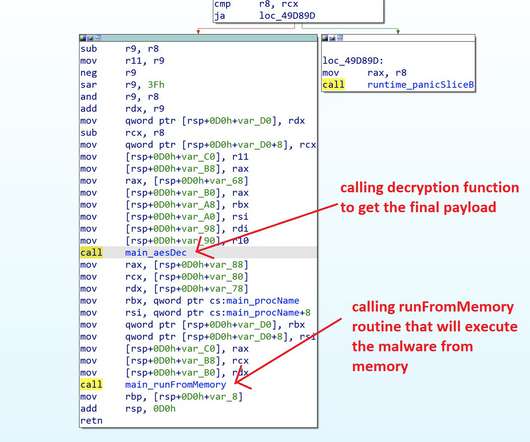
“The loader decrypts the malicious malware and executes it using memfd create (as described in this blog in 2018). Upon executing the code, it will ask the user the path for the payload to be encrypted and the password to be used for AES encryption to hide the malware within the loader.




































Let's personalize your content