A Cryptomining botnet abuses Bitcoin blockchain transactions as C2 backup mechanism
Security Affairs
FEBRUARY 24, 2021
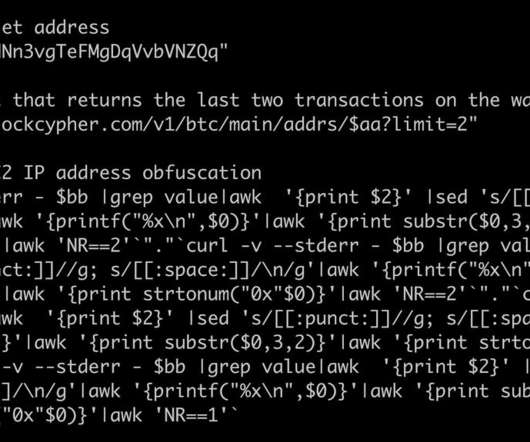
Crooks are exploiting BTC blockchain transactions to hide backup command-and-control (C2) server addresses for a cryptomining botnet. “A recent piece of malware from a known crypto mining botnet campaign has started leveraging Bitcoin blockchain transactions in order to hide its backup C2 IP address. . Pierluigi Paganini.










Let's personalize your content