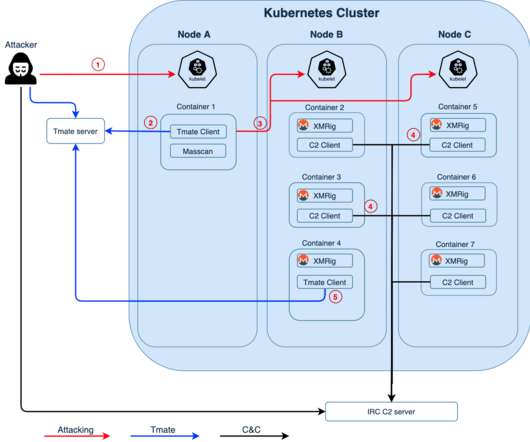
Blue Mockingbird Monero-Mining campaign targets web apps
Security Affairs
MAY 10, 2020
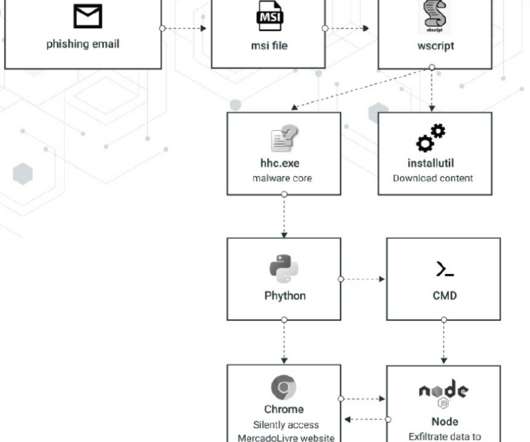
Crooks exploit CVE-2019-18935 deserialization vulnerability to achieve remote code execution in Blue Mockingbird Monero-Mining campaign. “Blue Mockingbird is the name we’ve given to a cluster of similar activity we’ve observed involving Monero cryptocurrency-mining payloads in dynamic-link library (DLL) form on Windows systems.”







































Let's personalize your content