TeamTNT is back and targets servers to run Bitcoin encryption solvers
Security Affairs
SEPTEMBER 19, 2022
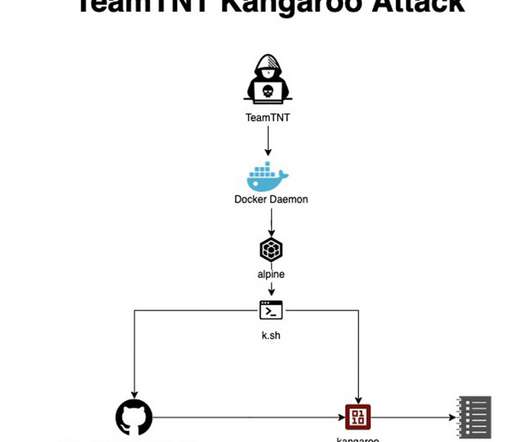
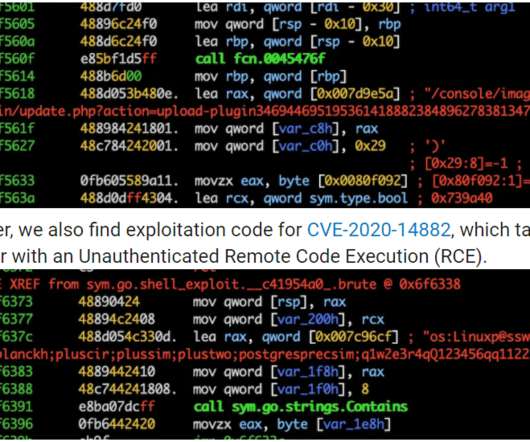
In the first week of September, AquaSec researchers identified at least three different attacks targeting their honeypots, the experts associated them with the cybercrime gang TeamTNT. The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and targets Docker installs. be on IP 93[.]95[.]229[.]203).”










Let's personalize your content