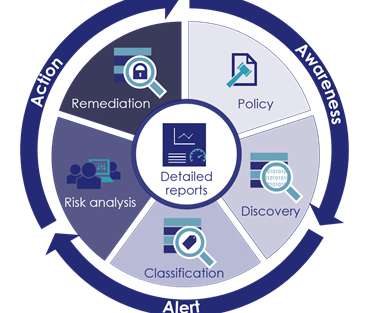
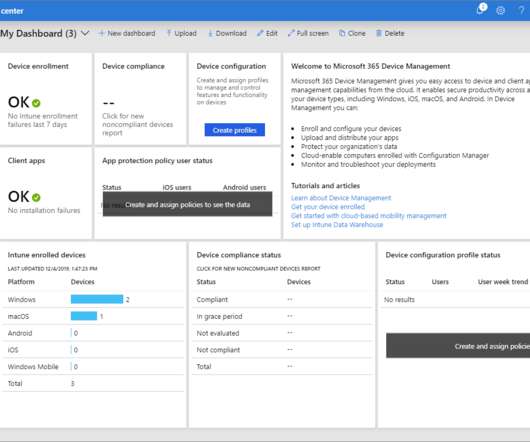
SHARING INTEL: Here’s why it has become so vital to prioritize the security-proofing of APIs
The Last Watchdog
NOVEMBER 30, 2021
Deriving the singular algorithms required to accomplish this heavy lifting is a tall order and couldn’t happen without the evolution of big data; today, it’s technically possible and economically feasible to store this extensive amount of data and apply processing power to extract security intelligence from it.













Let's personalize your content