Analysis: Emotet and Netwalker Takedowns
Data Breach Today
JANUARY 29, 2021
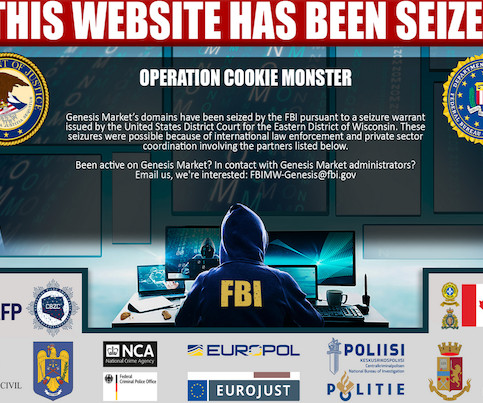
The latest edition of the ISMG Security Report features an analysis of this week’s police takedowns of Emotet and Netwalker cybercrime operations. Also featured: Updates on passwordless authentication and the use of deception technology.






































Let's personalize your content