Expert warns of Turtle macOS ransomware
Security Affairs
DECEMBER 1, 2023
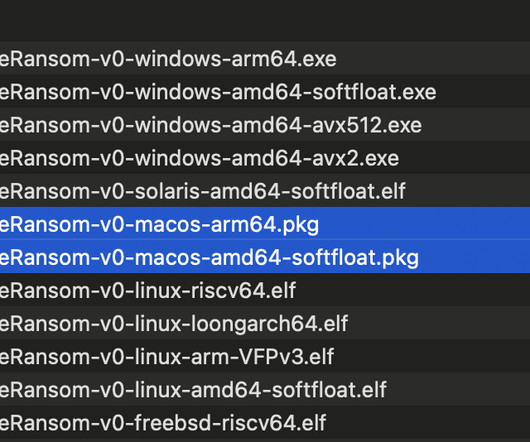
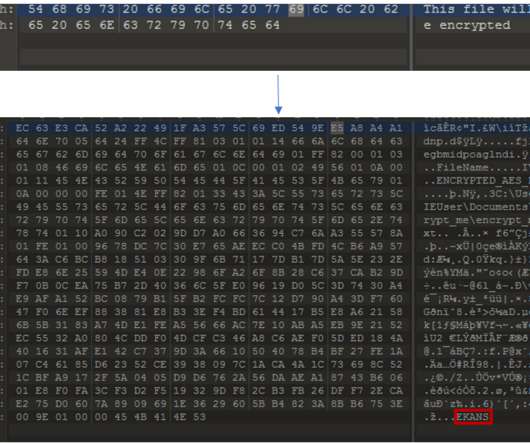
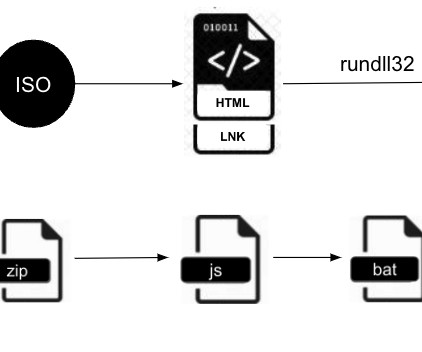
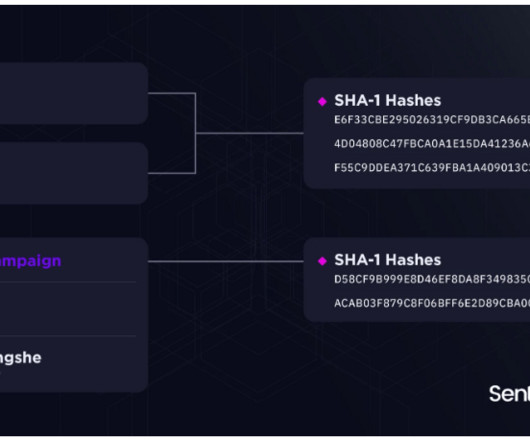
The popular cyber security researcher Patrick Wardle published a detailed analysis of the new macOS ransomware Turtle. The Turtle ransomware reads files into memory, encrypt them with AES (in CTR mode), rename the files, then overwrites the original contents of the files with the encrypted data. concludes the analysis.



























Let's personalize your content