Browser Makers and EU Face Off Over QWACs
Data Breach Today
APRIL 25, 2023
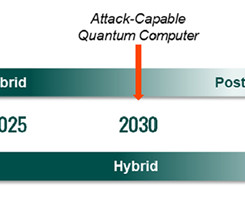
EU Set to Approve Revised ID Framework to Digitize Public Service Access by 2030 A European effort to wrest greater control over the infrastructure underpinning internet encryption has some security experts warning about degraded website security.















Let's personalize your content