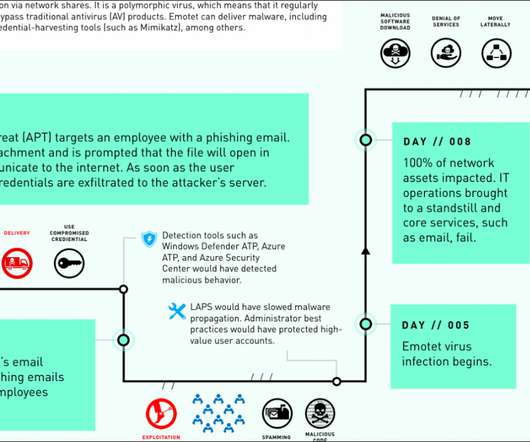
Microsoft’s case study: Emotet took down an entire network in just 8 days
Security Affairs
APRIL 4, 2020
‘We want to stop this hemorrhaging,’ an official would later say,” states DART case study report. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. The post Microsoft’s case study: Emotet took down an entire network in just 8 days appeared first on Security Affairs.





































Let's personalize your content