GUEST ESSAY: Where we stand on mitigating software risks associated with fly-by-wire jetliners
The Last Watchdog
AUGUST 29, 2023
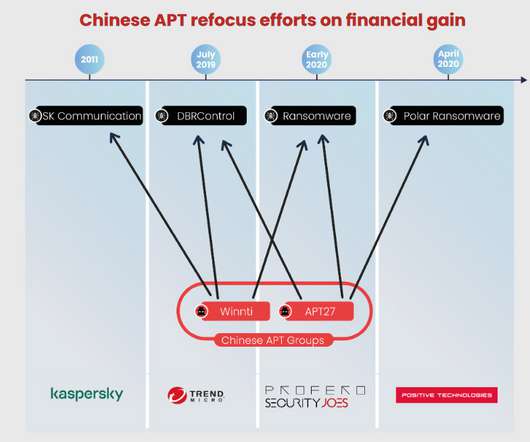
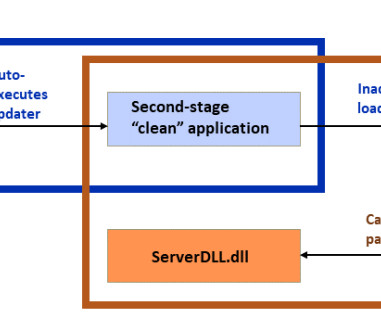
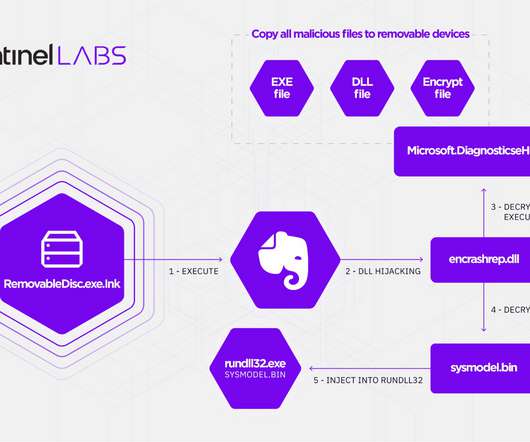
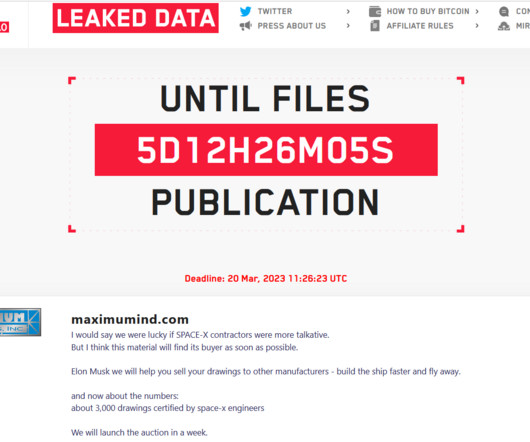
So watch out for weak encryption protocols, insufficient network segregation, or insecure user authentication mechanisms. Software gaps Similarly, the availability of onboard Wi-Fi services has become increasingly common in commercial aircraft so passengers can stay connected to the internet even during a long flight.










































Let's personalize your content