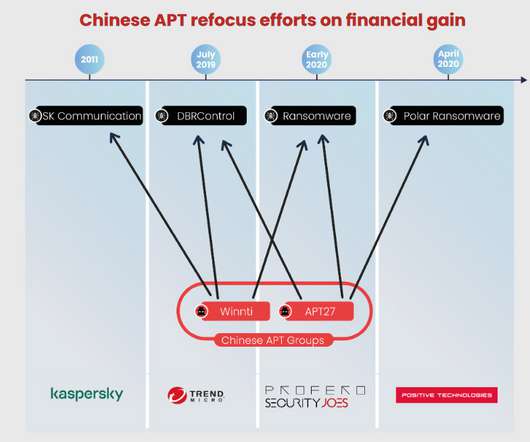
Experts linked ransomware attacks to China-linked APT27
Security Affairs
JANUARY 4, 2021
The APT group has been active since 2010, targeted organizations worldwide, including U.S. The hackers used the Windows drive encryption tool BitLocker to lock the servers. “Earlier this year, Security Joes and Profero responded to an incident involving ransomware and the encryption of several core servers.
























Let's personalize your content