Sophie Sayer on the IT Governance Partner Programme
IT Governance
FEBRUARY 14, 2024
The benefits of partnering with us, and our partner-exclusive event IT Governance launched its partner programme in 2017, which now includes more than 400 organisations. What else can partners expect from the event? Once a year, we also like to get all our partners in one room at our annual partner event.



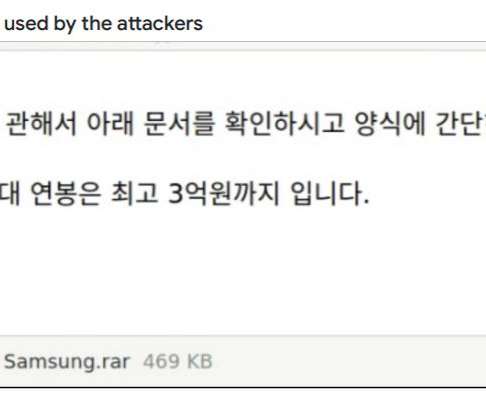































Let's personalize your content