The U.S. government today announced a coordinated crackdown against QakBot, a complex malware family used by multiple cybercrime groups to lay the groundwork for ransomware infections. The international law enforcement operation involved seizing control over the botnet’s online infrastructure, and quietly removing the Qakbot malware from tens of thousands of infected Microsoft Windows computers.

Dutch authorities inside a data center with servers tied to the botnet. Image: Dutch National Police.
In an international operation announced today dubbed “Duck Hunt,” the U.S. Department of Justice (DOJ) and Federal Bureau of Investigation (FBI) said they obtained court orders to remove Qakbot from infected devices, and to seize servers used to control the botnet.
“This is the most significant technological and financial operation ever led by the Department of Justice against a botnet,” said Martin Estrada, the U.S. attorney for the Southern District of California, at a press conference this morning in Los Angeles.
Estrada said Qakbot has been implicated in 40 different ransomware attacks over the past 18 months, intrusions that collectively cost victims more than $58 million in losses.
Emerging in 2007 as a banking trojan, QakBot (a.k.a. Qbot and Pinkslipbot) has morphed into an advanced malware strain now used by multiple cybercriminal groups to prepare newly compromised networks for ransomware infestations. QakBot is most commonly delivered via email phishing lures disguised as something legitimate and time-sensitive, such as invoices or work orders.
Don Alway, assistant director in charge of the FBI’s Los Angeles field office, said federal investigators gained access to an online panel that allowed cybercrooks to monitor and control the actions of the botnet. From there, investigators obtained court-ordered approval to instruct all infected systems to uninstall Qakbot and to disconnect themselves from the botnet, Alway said.
The DOJ says their access to the botnet’s control panel revealed that Qakbot had been used to infect more than 700,000 machines in the past year alone, including 200,000 systems in the United States.
Working with law enforcement partners in France, Germany, Latvia, the Netherlands, Romania and the United Kingdom, the DOJ said it was able to seize more than 50 Internet servers tied to the malware network, and nearly $9 million in ill-gotten cryptocurrency from QakBot’s cybercriminal overlords. The DOJ declined to say whether any suspects were questioned or arrested in connection with Qakbot, citing an ongoing investigation.
According to recent figures from the managed security firm Reliaquest, QakBot is by far the most prevalent malware “loader” — malicious software used to secure access to a hacked network and help drop additional malware payloads. Reliaquest says QakBot infections accounted for nearly one-third of all loaders observed in the wild during the first six months of this year.
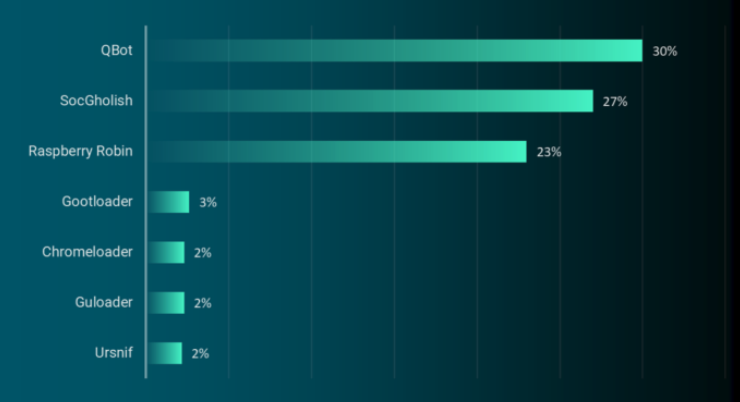
Qakbot/Qbot was once again the top malware loader observed in the wild in the first six months of 2023. Source: Reliaquest.com.
Researchers at AT&T Alien Labs say the crooks responsible for maintaining the QakBot botnet have rented their creation to various cybercrime groups over the years. More recently, however, QakBot has been closely associated with ransomware attacks from Black Basta, a prolific Russian-language criminal group that was thought to have spun off from the Conti ransomware gang in early 2022.
Today’s operation is not the first time the U.S. government has used court orders to remotely disinfect systems compromised with malware. In May 2023, the DOJ quietly removed malware from computers around the world infected by the “Snake” malware, an even older malware family that has been tied to Russian intelligence agencies.
Documents published by the DOJ in support of today’s takedown state that beginning on Aug. 25, 2023, law enforcement gained access to the Qakbot botnet, redirected botnet traffic to and through servers controlled by law enforcement, and instructed Qakbot-infected computers to download a Qakbot Uninstall file that uninstalled Qakbot malware from the infected computer.
“The Qakbot Uninstall file did not remediate other malware that was already installed on infected computers,” the government explained. “Instead, it was designed to prevent additional Qakbot malware from being installed on the infected computer by untethering the victim computer from the Qakbot botnet.”
The DOJ said it also recovered more than 6.5 million stolen passwords and other credentials, and that it has shared this information with two websites that let users check to see if their credentials were exposed: Have I Been Pwned, and a “Check Your Hack” website erected by the Dutch National Police.
Further reading:
–The DOJ’s application for a search warrant application tied to Qakbot uninstall file (PDF)
–The search warrant application connected to QakBot server infrastructure in the United States (PDF)
–The government’s application for a warrant to seize virtual currency from the QakBot operators (PDF)
–A technical breakdown from SecureWorks




* They removed the bot from tens of thousands of computers.
* In the past year alone, QakBot infected over 700,000 computers.
It is possible that malicious effects of QakBot will significantly diminish, but from those numbers I wouldn’t count on it.
One source I’ve seen says 700k bots were disconnected.
The FBI’s dismantling of the QakBot botnet this week was a major victory against the cybercriminals who have leveraged this insidious malware to enable ransomware attacks. By collaborating with international law enforcement and the private sector, the FBI has delivered a real blow to these digital extortion rings and made the internet safer for us all. Their efforts should be applauded, for once. It seems he malware’s code has be modified to get rid of itself so as it moves across the planet, all instances of QakBot should disappear.
The DOJ press release said that they uninstalled Qakbot from 700k computers including over 200k in the US. If the operators of the botnet are still free, after they collect their wits they may or may not decide to rebuild from scratch. It’ll be a lot of work and they are 9 million dollars poorer to start but they could try.
“Have I Been Pwned” comes up with one red flag @ VirusTotal.
And your point is exactly? … I think you need to do a bit more research and not jump to conclusions. Ever heard of a false positive?
If you dump the haveibeenpwned[dot]com[colon]443 url into the scanners on Quttera’s own website, the entity at VirusTotal that “red flags” said url, guess what it results in? Nada, zip, zilch. Minimal security risk, no malicious content detected!
If you access the community/comments section of VirusTotal regarding said url, you will see the same conclusion.
Security consultant Troy Hunt has been running the “Have I Been Pwned” website for over 10 years and it is recognised as a highly regarded data breach utility by security professionals and the general public globally.
Hello. I only pointed out what turned up with a VirusTotal scan–nothing more. Do you see any conclusions in my one line post? You seem to have drawn conclusions about what I intended. For the record, I visualize the Internet as “The Wild West,” exercise an abundance of caution, and avoid websites that come up with any red ink @ VirusTotal. But I don’t know enough to recommend my method to anyone.
So you spew absolute window-licking ignorance in public and the immediately back away when called on it.
What’s your end game here?
Because if you’re trying to look utterly regarded you nailed it.
Actual reptile behaviour, unalive yourself
wayooo chill bwo
“utterly regarded”
Oh snap. Utterly.
Thanks for the story, but look most other stories like this, information about how to recognize or determine whether an individual’s system is infected is nowhere to be found.
Nowhere? Did you get to the bottom?
The DOJ said it also recovered more than 6.5 million stolen passwords and other credentials, and that it has shared this information with two websites that let users check to see if their credentials were exposed: Have I Been Pwned, and a “Check Your Hack” website erected by the Dutch National Police.
Brian’s site is recognised as a source of security news, investigations and general mitigation, not technical remediation.
As he stated, if you ‘suspect’ some sort of infection/breach, enter your email address and/or phone number into the breach database websites noted above and if you are not listed as a Qakbot victim, great, your anti virus solution is doing it’s job.
If, however, you are one of the 6.5 million unlucky ones, you only have 2 choices; clean or rebuild. For the average home user (corporate remediation will be up to the assessment of internal security teams) on a Windows PC’s that you used these credentials on, I could only recommend a backup and a fresh bare metal install of your OS. Qakbot is a highly sophisticated piece of malware that possesses multiple attack vectors that has enabled it to evolve into a highly persistent threat and cleaning may prove fruitless. New build, no threat.
For credentials, you will also need to change passwords and, I’d suggest, even email addresses.
Microsoft Threat Intelligence Blog;
https://www.microsoft.com/en-us/security/blog/2021/12/09/a-closer-look-at-qakbots-latest-building-blocks-and-how-to-knock-them-down/
You can attempt a clean up here, if you know what you are doing, but a rebuild would be quicker and safer;
https://www.pcrisk.com/removal-guides/14443-qakbot-trojan
Now that more information is being revealed regarding this operation, as part of the take down and take over of Qbot servers, the FBI has issued uninstall commands across the botnet. Effectively meaning if your PC was infected with the strain, it has now been rendered inert. Huntress Labs have a vaccine file that is currently being rolled out to antivirus providers, to provide for future protection, as we speak.
As stated by Brian previously, check you credentials against the breach databases and change passwords/email if you are listed.
I am just curious how many of these are being monitored on by large corporations and acted upon. Bots are in use on a wide variety of platforms that i have seen. Will be interesting to see more about this and see what kind of popular response begins to take form.
Interesting read. just curious to see if large companies will begin to follow suite and attempt to defend themselves against OakBots or report them to the US Government. Currently learning about this in my security class.
I love the outcome of events here but it got me thinking, can this action not also be taken for other kinds of malware as well? Especially where critical infrastructure is concerned.
If it’s de-hacked by ABC agency and they get a court order then yeah. This isn’t the first time.
They do all kinds of mitigations for different types of malware, but not all threats are equal.
The neutralization of Snake malware through Operation Medusa was carried out in May 2023.
Doubt.
Derp?