Meet The Team Behind Mayhem: Come See Us At These Upcoming June 2023 Events
ForAllSecure
JUNE 7, 2023
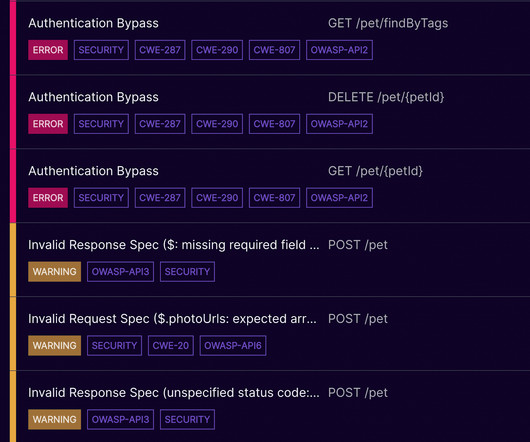
June is here, and we have exciting news queued up for the middle of the month. Stay tuned! Last month, we participated in GlueCon and hosted a webinar on uncovering vulnerabilities in open source software. We have 4 upcoming events planned for June 2023: Mayhem Unleashed Webinar: Discover our Next Generation Security Testing Solution DevSecOps Roundtable CyberSecurity Summit Hartford ForAllSecure APFT (Adversary, Penetration, and FuzzTesting) Training Read on to learn more about June’s eve














































Let's personalize your content