Cybercriminals behind the notorious Dridex and Locky ransomware have a new target in their sights – large retail, restaurant and grocery chains located in the US.
Researchers are warning the well-known financial criminal group TA505 is behind a new wave of email campaigns distributing personalized malware-laced attachments, a technique not previously associated with the threat actor.
Since November 15, the security firm Proofpoint said it has been tracking the email campaign targeting retailers with attachments that if opened attempt to install the FlawedAmmyy remote access trojan and Remote Manipulator System software.
FlawedAmmyy is a remote access trojan built from leaked source code of the popular remote desktop software Ammyy Admin. The Remote Manipulator System (RMS) client, similar to TeamViewer, is a remote desktop utility.
“We attributed these campaigns to TA505, the actor behind the largest Dridex and Locky ransomware campaigns of the last two years,” according to a Proofpoint technical write-up describing the campaigns posted Thursday.
Threat group TA505 has been active for the last four years. In July, Proofpoint identified TA505 for the first time using the FlawedAmmyy RAT in a widespread spam campaign distributing weaponized PDFs containing malicious SettingContent-ms files. Last month, Proofpoint attributed a malware campaign distributing the modular malware tRat.
“On December 3, 2018, we observed a TA505 campaign targeting almost exclusively retail, grocery, and restaurant chains. This campaign distributed tens of thousands of messages,” said Proofpoint of the most recent campaign.
Personalized Malicious Payload
TA505’s emails are designed to look like a messages generated and sent from a Ricoh brand printer containing a scanned document.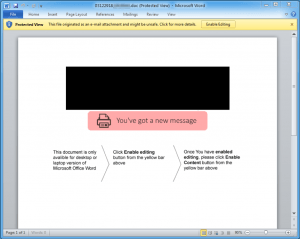
“The bogus scan was actually a malicious Microsoft Word attachment. The document attached was unique to the targeted company, and even contained the targeted company’s logo in the document lure (blurred in the figure with a black box),” researchers said.
An analysis of the attachment reveals the document contains a macro, that if enabled, downloads and executes an MSI file. An MSI file is a Microsoft Installer file, typically used to distribute Windows updates and installer updates for third-party Windows programs. The MSI file delivers the payloads: FlawedAmmyy RAT and the Remote Manipulator System software.
After the Word document is opened the message reads:
“Once You have enabled editing, please click Enable Content button from the yellow bar above.”
Proofpoint says this recent change in tactics for TA505 represents a larger shift among other similar threat actors.
The trend, researcher said, is a shift away from spray-and-pray campaigns to smaller, more targeted efforts that focus on downloaders, RATs, information stealers and banking trojans.
“Threat actors follow the money and, with dropping cryptocurrency values, the return on investment in better targeting, improved social engineering, and management of persistent infections now seems to be greater than that for large ‘smash and grab’ ransomware campaigns,” researchers said.










