Ransomware has become the most prevalent malicious software as hackers cash in on locking up expensive business critical systems and demanding a ransom, researchers warn.
Verizon’s 2018 Data Breach Investigations Report (DBIR), released Tuesday, said that ransomware attacks have doubled over the past year, and are now the top variety of malware found.
“[Ransomware] is now the most prevalent form of malware, and its use has increased significantly over recent years,” said Bryan Sartin, executive director security professional services at Verizon, in a statement. “What is interesting to us is that businesses are still not investing in appropriate security strategies to combat ransomware, meaning they end up with no option but to pay the ransom – the cybercriminal is the only winner here.”
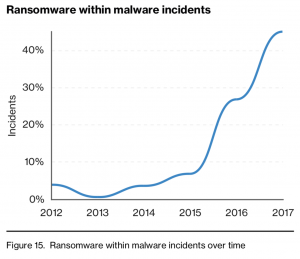
After analyzing over 53,000 security incidents – including 2,215 breaches – Verizon said that ransomware attacks made up 39 percent of the malware-specific incidents.
One trend driving crooks to ransomware attacks is the ability to target critical business systems – as opposed to desktops – which could do more damage to a company and generate more profits as extortion targets.
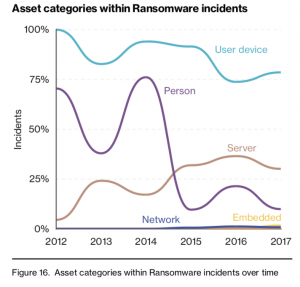
 Over time asset categories within ransomware incidents have grown beyond user devices to also include servers. Verizon said that’s because hackers realize that encrypting a file server or database is more damaging than a single user’s device.
Over time asset categories within ransomware incidents have grown beyond user devices to also include servers. Verizon said that’s because hackers realize that encrypting a file server or database is more damaging than a single user’s device.
“Lateral movement and other post-compromise activities often reel in other systems that are available for infection and obscuration,” according to Verizon.
Ransomware attacks are also appealing to attackers because they involve little or no risk or cost for the hackers themselves, and do not require a breach of confidentiality to meet their goal, said Verizon.
And that goal – money – is quickly becoming a top priority for many hackers. Verizon said in its report that 76 percent of breaches were financially motivated.
That was true with one of the most prominent instances of ransomware in 2017 – the WannaCry and NotPetya attacks in May. The WannaCry ransomware, which is estimated to have infected more than 300,000 systems across 150 countries, demanded a ransom of $300 for the decryption key. Meanwhile, NotPetya encrypted the master boot record and requested Bitcoin as the primary form of ransom payment.
In October, another ransomware campaign, BadRabbit, rocked the security industry – and showed just how much damage attackers were capable of when they targeted infrastructure rather than merely desktop systems. This campaign, linked to Russian Telebots, was launched using malware on websites in Russia, Ukraine, and Eastern Europe. Ukraine suffered the greatest disruption of critical web properties and infrastructure.
 Even more recently, in March 2018 the city of Atlanta was targeted in a ransomware attack impacting several of its departments and crippling government websites that process payments and relay court information. The city was asked to pay $51,000 in exchange for keys to decrypt systems.
Even more recently, in March 2018 the city of Atlanta was targeted in a ransomware attack impacting several of its departments and crippling government websites that process payments and relay court information. The city was asked to pay $51,000 in exchange for keys to decrypt systems.
Ransomware has been popular for attackers for awhile – in last year’s Verizon report, the company said that ransomware attacks had doubled as well.
To mitigate the likelihood of ransomware attacks, Verizon said in its report that people should make sure they have routine backups to fall back on, as well as segregate assets that are more critical to protect them and prioritize them with regard to business continuity.”
“As an industry, we have to help our customers take a more proactive approach to their security,” said Sartin in a statement. “Helping them to understand the threats they face is the first step to putting in place solutions to protect themselves.”‘
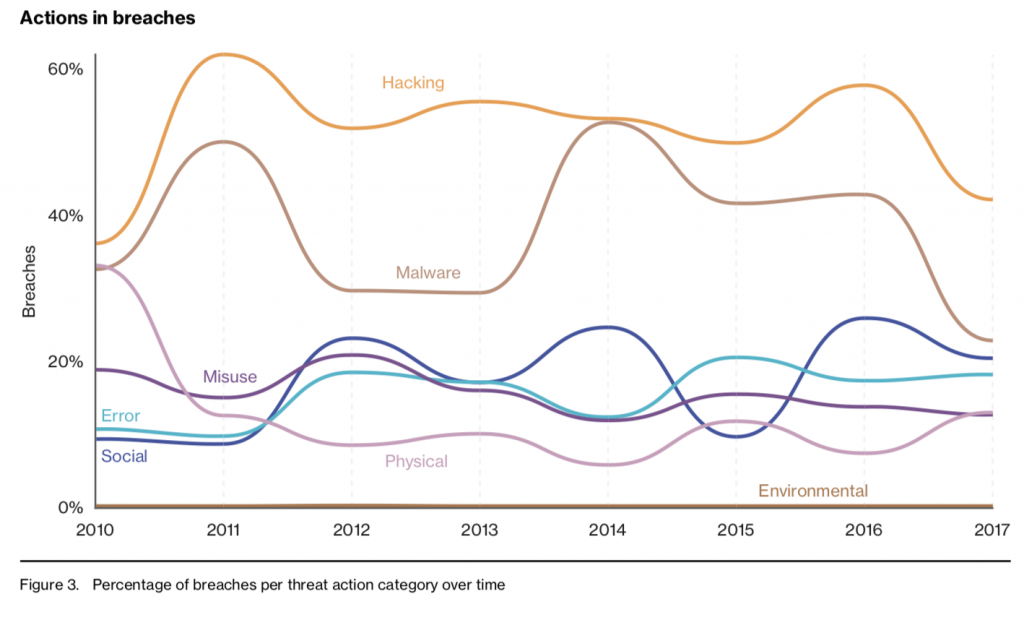
Overall, threats such as hacking, malware and social attacks (such as phishing) led to the most breaches over the past year, Verizon found.
Distributed denial of service (DDoS) attacks are another significant threat highlighted by Verizon’s 2018 report. “DDoS attacks can impact anyone and are often used as camouflage, often being started, stopped and restarted to hide other breaches in progress,” according to Verizon.
“Many attacks are now coming from cybercriminals who are financially motivated. Therefore, it’s no surprise that most attacks are reported against the Finance, Insurance and Retail industries,” said Sean Newman, director product management at Corero Network Security. “For online companies where it is critical to have 100 percent uptime, DDoS technology which can detect and automatically mitigate attacks, in real-time, should now be a must-have requirement.”