Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
Iran-Linked Phishing Campaign Targeted Medical Researchers
Proofpoint: Attackers Tried to Harvest Microsoft Office Credentials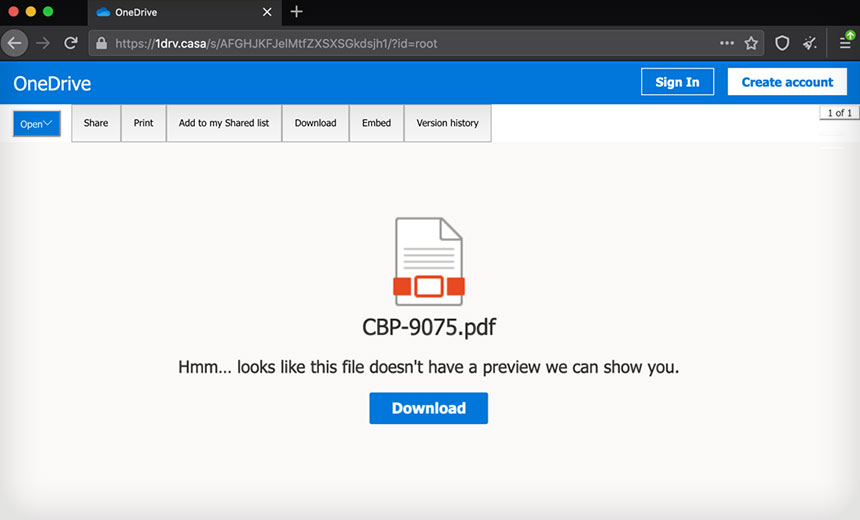
The Iranian-linked threat group TA453, also known as Charming Kitten and Phosphorus, conducted a phishing campaign, dubbed "BadBlood," in late 2020 that targeted senior U.S. and Israeli medical researchers in an attempt to obtain their Microsoft Office credentials, according to the security firm Proofpoint.
See Also: Digital Transformation: Better Ops, Agile Apps, Faster Business
Joshua Miller, a member of Proofpoint's threat research team, says the campaign coincided with heightened tensions between Iran and the U.S. and Israel, so it could have been part of a short-term effort to gather specific types of intelligence.
"BadBlood shifted targeting to medical research - genetics, oncology and neurology - and patient-related information. It remains to be seen whether this campaign represents a true shift or an outlier event," Miller says.
TA453 has been connected previously to the Islamic Revolutionary Guard Corps, which aligns its activity with the Iranian government and has concentrated its efforts on targeting dissidents, academics, diplomats and journalists. In November 2020, the U.S. Justice Department seized 27 website domains operated by the Corps that were used for a covert influence campaign targeting the U.S. and other nations.
In January, TA453 ran a text and email phishing campaign to spread malicious links in an attempt to steal email credentials in the U.S., Europe and the Persian Gulf region, security firm Certfa Lab reports. In September 2020, the gang used LinkedIn and WhatsApp messages to contact potential victims to build trust and persuade them to visit a phishing page, according to the security firm ClearSky.
"While Proofpoint cannot independently attribute TA453 to the IRGC [Islamic Revolutionary Guard Corps], the tactics and techniques observed in BadBlood continue to mirror those used in historic TA453 campaigns and the overall targeting of TA453 campaigns detected by Proofpoint appear to support IRGC intelligence collection priorities," the new report says.
The BadBlood Campaign
In the BadBlood phishing campaign, which took place in December 2020, the attackers attempted to entice victims to visit a fake website where the attackers would steal the victims' Microsoft Office credentials, Proofpoint says. The attackers used a fake Gmail account - "zajfman.daniel[@]gmail.com" - that purported to be owned by a prominent Israeli physicist.
The fake Gmail account sent messages with the subject "Nuclear weapons at a glance: Israel" that contained social engineering lures relating to Israeli nuclear capabilities. A link led to a TA453-controlled domain that spoofed Microsoft's OneDrive cloud storage service and contained the image of a PDF document named CBP-9075, the report says.
If the victim attempted to view the PDF, they were sent to a fake Microsoft login page that harvested any disclosed information. As a final step, the attackers tried to make the theft appear legitimate by taking the victim to a page containing a document labeled "Nuclear weapons at a glance: Israel," which reflects the email's original subject line, the report says.
"Although Proofpoint does not currently have further visibility into how TA453 used any credentials obtained from this specific campaign, public reporting from CERTFA [Computer Emergency Response Team in Farsi] indicates TA453 has previously used harvested credentials to exfiltrate email inbox contents," Miller writes.
TA453 has used stolen credentials for phishing attacks in other campaigns, the report notes.
A Narrow Target List
Proofpoint says that the TA453 phishing campaign in December targeted fewer than 25 senior-level staffers at various medical research organizations located in the U.S. and Israel. The staffers all worked in the fields of genetics, oncology or neurology fields.
Researchers say the campaign may demonstrate that:
- A subset of TA453 has a mission to collect specific medical information related to research on genetics, oncology or neurology;
- The attackers wanted to obtain patient information on the targeted medical personnel;
- The attackers wanted to obtain credentials for use in further phishing campaigns.
Another possibility, according to the report: "BadBlood is aligned with an escalating trend globally of medical research being increasingly targeted by espionage motivated focused threat actors."






















