Researchers are warning of an upward surge in social-engineering lures in malicious emails that promise victims financial relief during the coronavirus pandemic.
The slew of campaigns piggy-back on news of governments mulling financial relief packages, in response to the economic stall brought on by consumers social distance themselves. This latest trend shows cybercriminals continuing to look to the newest developments in the coronavirus saga as leverage for phishing campaigns, targeted emails spreading malware and more.
“These campaigns use the promise of payments by global governments and businesses (specifically financial institutions) aimed at easing the economic impact of the ongoing pandemic to urge users to click links or download files,” said Proofpoint researchers, in analysis released Wednesday.

One credential-phishing campaign has been spotted primarily targeting U.S. healthcare and higher-education organizations (as well as the technology industry, including information-security companies), with a message purporting to be from their payroll departments.
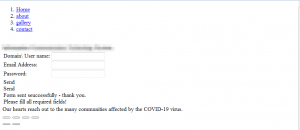
The emails, titled “General Payroll !” explain that the Trump administration “is considering” sending most American adults a check to help stimulate the economy.
 “The Trump administration is considering sending most American adults a check for $1,000 as part of the efforts to stimulate the economy and help workers whose jobs have been disrupted by business closures because of the pandemic,” says the message. “All staff/faculty & employee include student are expected to verify their email account for new payroll directory and adjustment for the month of March benefit payment.”
“The Trump administration is considering sending most American adults a check for $1,000 as part of the efforts to stimulate the economy and help workers whose jobs have been disrupted by business closures because of the pandemic,” says the message. “All staff/faculty & employee include student are expected to verify their email account for new payroll directory and adjustment for the month of March benefit payment.”
Researchers said that these emails come with plenty of red flags, including their “crude design,” with clear grammatical and spelling errors as can be seen above. The messages also use a basic web page that’s clearly branded by a free website maker for its phishing landing page.
The message asks recipients to verify their email accounts through a malicious link (called the “MARCH-BENEFIT secure link”) that directs them to a phishing page. This phishing page then asks for their usernames, email addresses and passwords tied to their employee benefits.
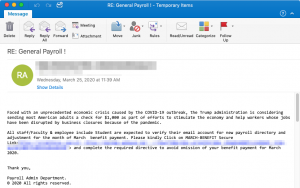
Researchers pointed to similar phishing campaigns in Australia and the U.K. In Australia, a campaign was discovered using emails claiming to be from a major Australian newspaper and using the subject line, “Government announces increased tax benefits in response to the coronavirus.” These email messages contain a PDF attachment with an embedded URL that leads to a phishing page, where victims are asked to input their Microsoft OneDrive credentials.
In the U.K., a large email campaign was uncovered targeting manufacturing, technology, transportation, healthcare, aerospace, retail, energy, technology, business services and hospitality companies. The campaign emails claim to be from a major (unnamed) United Kingdom bank. It offers 300 Singapore dollars (approximately $210 USD) as financial support, and tells the recipient to “Start Here” to claim the money by clicking on a link. That then leads them to the attacker-controlled landing page that asks for their name, address and credit-card number.
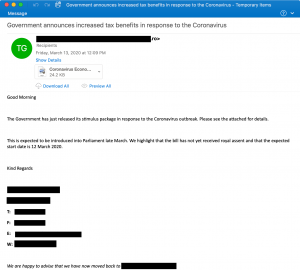 Another, smaller campaign targets technology and IT organizations, purporting to be from the World Health Organization (WHO) and the International Monetary Fund (IMF). These emails, sent with a subject line of “COVID 19 : Relief Compensation,” tells recipients they have been “randomly selected to be compensated financially due to the outbreak of the COVID-19 Epidemic outbreak” and asks them to learn more by clicking on an fake Microsoft Excel-branded attachment that gathers emails and passwords.
Another, smaller campaign targets technology and IT organizations, purporting to be from the World Health Organization (WHO) and the International Monetary Fund (IMF). These emails, sent with a subject line of “COVID 19 : Relief Compensation,” tells recipients they have been “randomly selected to be compensated financially due to the outbreak of the COVID-19 Epidemic outbreak” and asks them to learn more by clicking on an fake Microsoft Excel-branded attachment that gathers emails and passwords.
Attackers continue to leverage coronavirus-themed cyberattacks as panic around the global pandemic continues – including malware attacks, booby-trapped URLs and credential-stuffing scams. Researchers warned that users should continue to be on the lookout for phishing emails playing into fears around the coronavirus pandemic.
Zeus Sphinx for instance was recently spotted joining the growing fray of COVID-19-themed phishing and malspam campaigns, using a government-assistance lure.
“The ongoing shift to coronavirus-themed messages and campaigns is truly social engineering at scale, and these recent payment-related lures underscore that threat actors are paying attention to new developments,” researchers said. “We anticipate threat actors will continue modifying their strategies as the news surrounding COVID-19 shifts.”
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.