The SideWinder advanced persistent threat (APT) group has mounted a fresh phishing and malware initiative, using recent territory disputes between China, India, Nepal and Pakistan as lures. The goal is to gather sensitive information from its targets, mainly located in Nepal and Afghanistan.
According to an analysis, SideWinder typically targets victims in South Asia and surroundings – and this latest campaign is no exception. The targets here include multiple government and military units for countries in the region researchers said, including the Nepali Ministries of Defense and Foreign Affairs, the Nepali Army, the Afghanistan National Security Council, the Sri Lankan Ministry of Defense, the Presidential Palace in Afghanistan and more.
The effort mainly makes use of legitimate-looking webmail login pages, aimed at harvesting credentials. Researchers from Trend Micro said that these pages were copied from their victims’ actual webmail login pages and subsequently modified for phishing. For example, “mail-nepalgovnp[.]duckdns[.]org” was created to pretend to be the actual Nepal government’s domain, “mail[.]nepal[.]gov[.]np”.
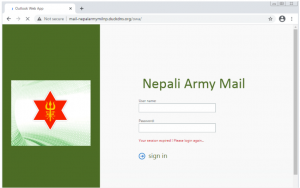
Convincing-looking phishing page. Source: Trend Micro.
Interestingly, after credentials are siphoned off and the users “log in,” they are either sent to the legitimate login pages; or, they are redirected to different documents or news pages, related either to COVID-19 or political fodder.
Researchers said some of the pages include a May article entitled “India Should Realise China Has Nothing to Do With Nepal’s Stand on Lipulekh” and a document called “Ambassador Yanchi Conversation with Nepali_Media.pdf,” which provides an interview with China’s ambassador to Nepal regarding Covid-19, the Belt and Road Initiative, and territorial issues in the Humla district.
Espionage Effort
The campaign also includes a malware element, with malicious documents delivered via email that are bent on installing a cyberespionage-aimed backdoor. And, there was evidence that the group is planning a mobile launch to compromise wireless devices.
“We identified a server used to deliver a malicious .lnk file and host multiple credential-phishing pages,” wrote researchers, in a Wednesday posting. “We also found multiple Android APK files on their phishing server. While some of them are benign, we also discovered malicious files created with Metasploit.”
Email Infection Routine
On the email front, researchers found that many malicious initial files are being used in the campaign, including a .lnk file that in turn downloads an .rtf file and drops a JavaScript file on the target’s computer; and a .zip file containing a .lnk file that in turn downloads an .hta file (with JavaScript).
“All of these cases end up with either the downloading or dropping of files and then the execution of JavaScript code, which is a dropper used to install the main backdoor plus stealer,” researchers explained.
The downloaded .rtf files in the chain meanwhile exploit the CVE-2017-11882 vulnerability; the exploit allows attackers to automatically run malicious code without requiring user interaction.
The flaw affects all unpatched versions of Microsoft Office, Microsoft Windows and architecture types dating back to 2000. While it was patched in November 2017, Microsoft warned as late as last year that email campaigns were spreading malicious .rtf files boobytrapped with an exploit for it.
“The CVE-2017-11882 vulnerability was fixed in 2017, but to this day, we still observe the exploit in attacks,” Microsoft Security Intelligence tweeted in 2019. “Notably, we saw increased activity in the past few weeks. We strongly recommend applying security updates.”
In this case, the boobytrapped .rtf drops a file named 1.a, which is a JavaScript code snippet. This places the backdoor and stealer into a folder in ProgramData and directly executes it, or creates a scheduled task to execute the dropped files at a later time, Trend Micro found.
“The content of the newly created folder contains a few files, including Rekeywiz, which is a legitimate Windows application,” analysts explained. “This application loads various system DLL libraries, including…a fake DUser.dll [that] decrypts the main backdoor + stealer from the .tmp file in the same directory.”
After decryption, the payload collects system information and uploads it to the command-and-control server (C2), before setting about stealing targeted file types.
“[This] includes information such as privileges, user accounts, computer system information, antivirus programs, running processes, processor information, operating system information, time zone, installed Windows updates, network information, list of directories in Users\%USERNAME%\Desktop, Users\%USERNAME%\Downloads, Users\%USERNAME%\Documents, Users\%USERNAME%\Contacts, as well as information on all drives and installed apps,” Trend Micro said.
Mobile Campaign Pending?
The researchers saw several mobile apps that were under development. Some contained no malicious code (yet); for instance, a mobile app called “OpinionPoll” was lurking on the server, purporting to be a survey app for gathering opinions regarding the Nepal-India political map dispute.
Others contained malicious capabilities but seemed unfinished.
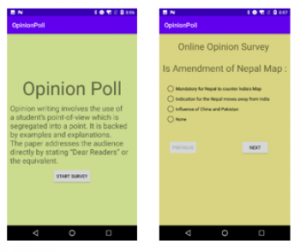
Several mobile apps appear to be under development. Source: Trend Micro.
“While we were unable to retrieve the payload, according to the Manifest that requests numerous privacy-related permissions like location, contacts, call logs, etc., we can infer that it goes after the user’s private data,” researchers wrote.
SideWinder has used malicious apps as part of its operation before, disguised as photography and file manager tools to lure users into downloading them. Once downloaded into the user’s mobile device, they exploited the CVE-2019-2215 and MediaTek-SU vulnerabilities for root privileges.
In this case, “we believe these applications are still under development and will likely be used to compromise mobile devices in the future,” researchers noted.
SideWinder has active throughout late 2019 and in 2020, according to the firm, having been spotted using the Binder exploit to attack mobile devices. Trend Micro said the group also launched attacks earlier this year against Bangladesh, China and Pakistan, using lure files related to COVID-19.
“As seen with their phishing attacks and their mobile device tools’ continuous development, SideWinder is very proactive in using trending topics like COVID-19 or various political issues as a social-engineering technique to compromise their targets,” the firm concluded. “Therefore, we recommend that users and organizations be vigilant.”
Put Ransomware on the Run: Save your spot for “What’s Next for Ransomware,” a FREE Threatpost webinar on Dec. 16 at 2 p.m. ET. Find out what’s coming in the ransomware world and how to fight back.
Get the latest from John (Austin) Merritt, Cyber Threat Intelligence Analyst at Digital Shadows; Limor Kessem, Executive Security Advisor, IBM Security; and Israel Barak, CISO at Cybereason, on new kinds of attacks. Topics will include the most dangerous ransomware threat actors, their evolving TTPs and what your organization needs to do to get ahead of the next, inevitable ransomware attack. Register here for the Wed., Dec. 16 for this LIVE webinar.











