SAN FRANCISCO – Researchers have identified the hacking group behind several widescale business email compromise (BEC) attacks gouging the maritime shipping industry millions of dollars since last year. Attackers are taking advantage of the industry’s lax security and the use of outdated computers, according to a report released here at the RSA Conference Wednesday.
Researchers from the Dell SecureWorks Counter Threat Unit dubbed the BEC group Gold Galleon. The researchers estimate that Gold Galleon has specifically targeted the shipping industry in an attempt to steal at least $3.9 million between June 2017 and January 2018.
Gold Galleon’s targets include maritime shipping organizations – such as companies providing ship management services, port services and cash to master services. Because the shipping industry is globally dispersed and operates in different time zones, they are completely reliant on email for communication – and thus a “low hanging fruit” for BEC scams, said James Bettke, security researcher at SecureWorks, who led the research into the group.
“There’s a couple reasons [Gold Galleon] would target this industry… it’s a perfect storm between the lack of security and an interesting cultural piece,” said Bettke in an interview with Threatpost. “Many shipping companies that are very small are not worried about security – they don’t have two factor authentication and are running Windows XP. The second piece is that many of these small companies are doing international business and communicating primarily with email, so it’s hard to know if someone is being impersonated.”
SecureWorks found that Gold Galleon appears to be a group of at least 20 cybercriminals, who likely are based in Nigeria. The criminals work together to carry out various parts of the BEC campaigns – from the initial compromise, to monitoring accounts.
Gold Galleon identifies target emails by collecting publicly available contact information, such as the company’s website as well as leveraging marketing tools BoxxerMail or Email Extractor to scrape email addresses from companies’ websites, according to SecureWorks.
After gaining entry into a target’s inbox, the cybercriminals will also extract a recipient’s contacts through a tool called EmailPicky.
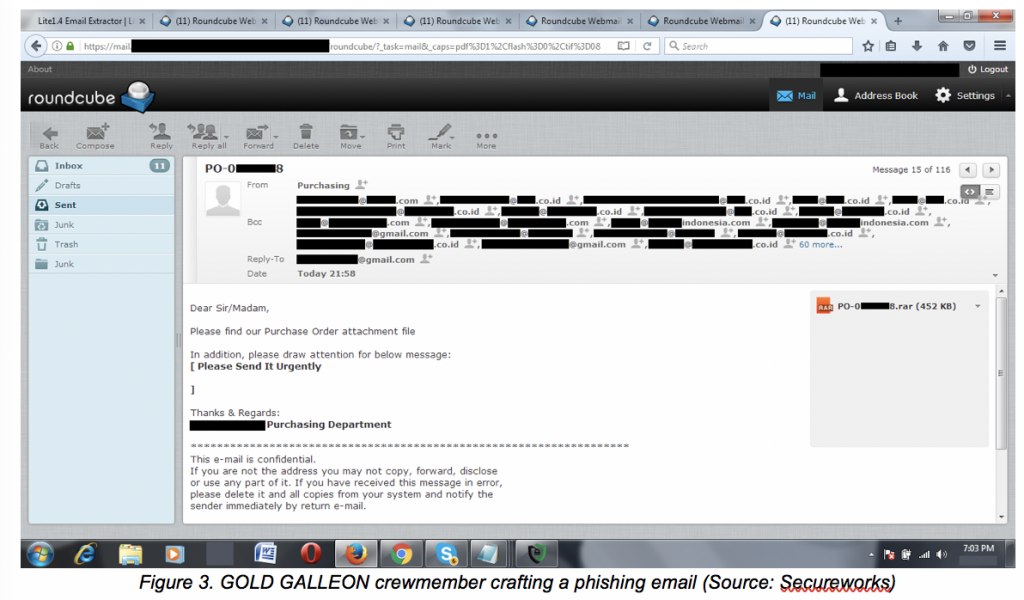
Gold Galleon uses spearphishing techniques with malicious attachments to compromise their victims.
These attachments contain a remote access tool with keylogging and password stealing functionality: “Tools deployed by GOLD GALLEON include the Predator Pain, PonyStealer, Agent Tesla and Hawkeye keyloggers. All of the malware leveraged by GOLD GALLEON is readily available from online hacking markets,” according to SecureWorks’ report.
Once the group compromises the email accounts, members of the crew monitor the employees’ inbox to identify emails for ongoing business transactions.
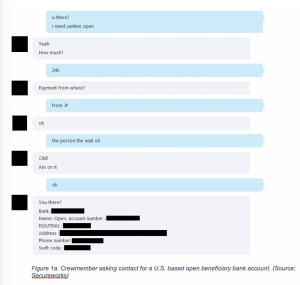
When it is time for payment details to be relayed to the buyer through an invoice, the threat actor intercepts the seller’s email and changes the destination bank account on the invoice to their money mule account.
“In order to impersonate a buyer or seller in a particular transaction, GOLD GALLEON and other BEC groups, have been observed purchasing domains which closely resemble the buyer or seller’s company name, they refer to this as ‘cloning,'” according to SecureWorks.
The group uses a range of commodity remote access tools that have keylogging and password-stealing functionality to steal email account credentials. Senior members of Gold Galleon will also routinely test malware on their own systems and tracks detection rates via online virus scanners, Bettke said.
After sifting through usernames and passwords for the group, SecureWorks also linked Gold Galleon to a popular fraternity in Nigeria called the Buccaneer Confraternity or the National Association of Seadog.
The Bucaneers Confraternity was originally established in Nigeria to support human right in the country – but reports suggest that a small subset of the group could engage in criminal activity.
To mitigate attacks, SecureWorks suggests that potential victims implement two factor authentication, and inspect corporate email control panels for suspicious redirect rules.
“The malware they use is very unsophisticated,” said Bettke. “I suggest companies in the maritime industry adopt two factor authentication and stronger accounting controls, so if someone out of the blue asks to change accounts, company employees should get on the phone instead of corresponding via email.”