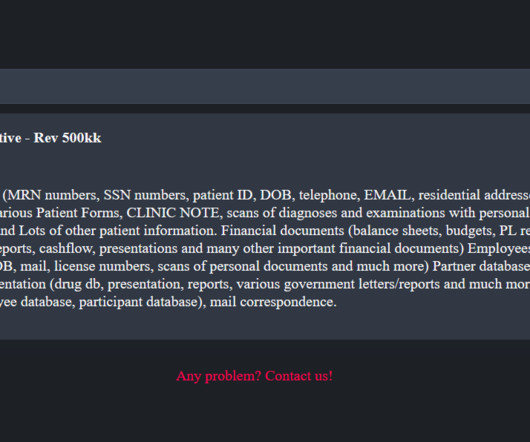
Ransomware Groups: Trust Us. Uh, Don't.
Data Breach Today
MARCH 18, 2024
Review of Attacks Finds Inconsistent Data Leaks and Victim Naming, Broken Promises Ransomware groups hope threats are enough to sway victims so they don't have to follow through.















































Let's personalize your content