Researchers are warning of an ongoing phishing attack that’s targeting the credentials of more than 100 high-profile executives at a German multinational corporation that’s tasked with procuring coronavirus medical gear for Germany.
The company, left unnamed by researchers, is part of a task force created March 30 by the German government and the private sector to procure personal protective equipment (PPE) for healthcare workers on the front lines of COVID-19, such as face masks and medical equipment. The task force consists of nine companies, including car manufacturer Volkswagen, pharmaceutical company Bayer, airline Lufthansa, chemical firm BASF and shipping company DHL, who are leveraging their access to foreign markets to purchase and deliver PPE to German ministries.
Researchers who discovered the phishing attack believe its perpetrators may be targeting multiple firms, and third-party supply chain partners, associated with the task force.
“The threat actors behind this campaign targeted more than 100 high ranking executives in management and procurement roles within this organization and its third-party ecosystem,” said Claire Zaboeva, cyber-threat researcher with IBM X-Force, in a Monday analysis. “Given the extensive targeting observed of this supply chain, it’s likely that additional members of the task force could be targets of interest in this malicious campaign, requiring increased vigilance.”
On March 30 (the same day the task force was created), “suspicious activity” was discovered related to the phishing attack. Zaboeva told Threatpost that the activity was uncovered in the wild and a copy of the initial phishing emails is not available.
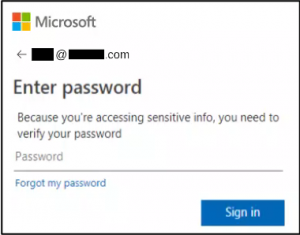
The emails contained URLs that redirect the email recipients to a fake, attacker-controlled Microsoft login page that’s designed to steal user credentials. Once passwords have been inputted, they are then exfiltrated to several different email accounts hosted on Russian email service Yandex.
While it is unclear how many of the phishing attacks were successful, the attack could open the door to credential harvesting, which could allow threat actors to access victims’ email accounts. From there, they could collect or exfiltrate data of interest, or move laterally through the network for other malicious purposes, researchers said.
Researchers tracked this suspicious activity to a Russia-based IP address (178[.]159[.]36[.]183). Overall, more than 280 URLs were found to be tied to that IP address. More than a third of these included Base64-encoded email addresses belonging to targets at the firm and its third-party supply chain partners.
Of those emails, half belong to the target company’s operations, finance and procurement executives. The other half belong to executives at third-party partners of the firm, including European and American companies associated with chemical manufacturing, aviation and transport, medical and pharmaceutical manufacturing, finance, oil and gas, and communications, researchers said. About 40 companies have been subject to the targeted activity worldwide, Zaboeva told Threatpost.
“Based on our analysis, attackers likely intended to compromise a single international company’s global procurement operations, along with their partner environments devoted to a new government-led purchasing and logistics structure,” said researchers.
Researchers notified CERT BUND, which operates Germany’s national IT Situation Centre, about the activity. As many organizations worldwide ramp up PPE production to support medical professionals on the front lines of the coronavirus, they are part of an emerging “high-value target group” whose reliance on technology to enable business practices “provides a potential means of compromise to malicious cyber actors,” warned researchers.
The FBI, for instance, in April warned that threat actors are taking advantage of efforts to procure PPE and critical equipment such as ventilators, with new business email compromise (BEC) and other scams aimed at defrauding those seeking the supplies.