Researchers say that the North Korea-linked Andariel hacking group may be looking to switch up its targets, based on key changes in its script found on recently compromised websites.
The Andariel group is associated with the infamous Lazarus Group, North Korea’s cyber-espionage unit. Andariel has been particularly active over the past few months, targeting mainly South Korean victims. According to South Korean security researchers at IssueMakersLab, the group has mainly been using a zero-day exploit on Microsoft’s ActiveX software framework, enabling watering-hole attacks on South Korean websites.
However, Trend Micro researchers noticed at the end of June 2018 that the group was injecting their script into four targeted South Korean websites for reconnaissance purposes – and, the script has striking differences from Andariel has used before. That could show that it may be trying to collect different ActiveX object information, and ultimately expand its target base, researchers said on Monday.
“In the earlier case, the group collected targeted ActiveX objects on users’ Internet Explorer browsers before they used the zero-day exploit,” Joseph Chen, fraud researcher with Trend Micro, said in a post. “This was possibly part of their reconnaissance strategy, to find the right targets for their exploit. Based on this, we believe it’s likely that the new targeted ActiveX objects we found could be their next targets for a watering-hole exploit attack.”
Trend Micro researchers said they found the injected script June 21, and that it was similar to the sample Andariel previously used, including a string of attacks in May. The injected script was on the website of a Korean non-profit organization, as well as three South Korean local government labor union websites.
The script was used to collect information from visitors’ browser: browser type, system language, Flash Player version, Silverlight version, and multiple ActiveX objects. Chen said the code had similar obfuscation and structure to the samples previously found from the Andariel. 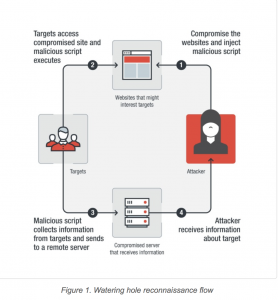 However, interestingly, Chen said that the script was trying to detect two ActiveX objects not targeted in previously viewed samples.
However, interestingly, Chen said that the script was trying to detect two ActiveX objects not targeted in previously viewed samples.
One was related to digital rights management software from a South Korean document-protection security vendor; while the other is related to a South Korea-based voice conversion software company. Both are used by local governments and public institutions, researchers said.
The verification process in the older script is also different from the ActiveX detection, which was only for the Internet Explorer browser – but now can be performed on other browsers, Chen said.
“In the script found in June, the websocket verification could also be performed on other browsers like Chrome and Firefox,” researchers said. “This shows that the attacker has expanded his target base, and is interested in the software itself and not just their ActiveX objects. Based on this change, we can expect them to start using attack vectors other than ActiveX.”
The reconnaissance lasted until June 27; and the websites have been notified about the compromise, said researchers.
“Reconnaissance is the stage where attackers collect information from potential targets to help them determine what tactics will work,” Chen said. “These new developments from the Andariel group give us an idea of their plans, although we cannot make specific assumptions about their strategy.”










