I'm always on the quest for real-world malware samples that help educate professionals how to analyze malicious software. As techniques and technologies change, I introduce new specimens and retire old ones from the reverse-engineering course I teach at SANS Institute. Here are some of the legacy samples that were once present in FOR610 materials. Though these malicious programs might not appear relevant anymore, aspects of their functionality are present even in modern malware.
A Backdoor with a Backdoor
To learn fundamental aspects of code-based and behavioral malware analysis, the FOR610 course examined Slackbot at one point. It was an IRC-based backdoor, which it's author "slim" distributed as a compiled Windows executable without source code.
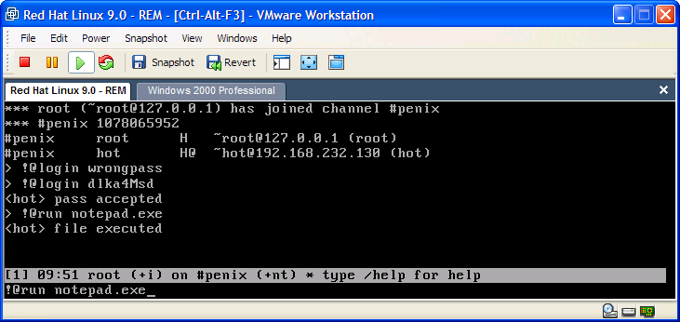
Dated April 18, 2000, Slackbot came with a builder that allowed its user to customize the name of the IRC server and channel it would use for Command and Control (C2). Slackbot documentation explained how the remote attacker could interact with the infected system over their designated channel and included this taunting note:
“don't bother me about this, if you can't figure out how to use it, you probably shouldn't be using a computer. have fun. --slim”
Those who reverse-engineered this sample discovered that it had undocumented functionality. In addition to connecting to the user-specified C2 server, the specimen also reached out to a hardcoded server irc.slim.org.au that "slim" controlled. The channel #penix channel gave "slim" the ability to take over all the botnets that his or her "customers" were building for themselves.
Turned out this backdoor had a backdoor! Not surprisingly, backdoors continue to be present in today's "hacking" tools. For example, I came across a DarkComet RAT builder that was surreptitiously bundled with a DarkComet backdoor of its own.
You Are an Idiot
The FOR610 course used an example of a simple malevolent web page to introduce the techniques for examining potentially-malicious websites. The page, captured below, was a nuisance that insulted its visitors with the following message:
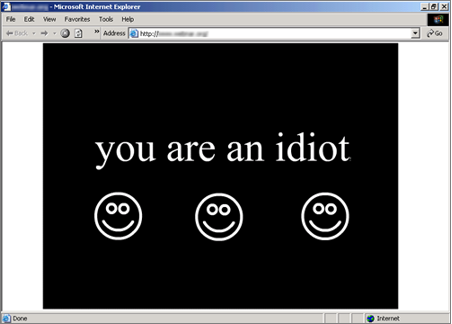
When the visitor attempted to navigate away from the offending site, its JavaScript popped up new instances of the page, making it very difficult to leave. Moreover, each instance of the page played the following jingle on the victim's speakers. "You are an idiot," the song exclaimed. "Ahahahahaha-hahahaha!" The cacophony of multiple windows blasting this jingle was overwhelming.
A while later I came across a network worm that played this sound file on victims' computers, though I cannot find that sample anymore. While writing this post, I was surprised to discover a version of this page, sans the multi-window JavaScript trap, residing on www.youareanidiot.org. Maybe it's true what they say: good joke never gets old.
Clipboard Manipulation
When Flash reigned supreme among banner ad technologies, the FOR610 course covered several examples of such forms of malware. One of the Flash programs we analyzed was a malicious version of the ad pictured below:

At one point, visitors to legitimate websites, such as MSNBC, were reporting that their clipboards appeared "hijacked" when the browser displayed this ad. The advertisement, implemented as a Flash program, was using the ActionScript setClipboard function to replace victims' clipboard contents with a malicious URL.
The attacker must have expected the victims to blindly paste the URL into messages without looking at what they were sharing. I remembered this sample when reading about a more recent example of malware that replaced Bitcoin addresses stored in the clipboard with the attacker's own Bitcoin address for payments.
As malware evolves, so do our analysis approaches, and so do the exercises we use in the FOR610 malware analysis course. It's fun to reflect upon the samples that at some point were present in the materials. After all, I've been covering this topic at SANS Institute since 2001. It's also interesting to notice that, despite the evolution of the threat landscape, many of the same objectives and tricks persist in today's malware world.