A phishing campaign that Microsoft security researchers have been tracking for about a year highlights not only the ongoing success of social engineering efforts by hackers to compromise systems, but also the extent to which the bad actors will go to cover their tracks while stealing user credentials.
In a blog post, researchers with the Microsoft 365 Defender Threat Intelligence Team outlined how the cybercriminals changed tactics to evade detection, going so far as to change their obfuscation and encryption mechanisms an average of every 37 days – including using older encryption methods like Morse code.
The hackers make these relatively rapid changes in hopes of ensuring that their phishing efforts will go undetected for as long as possible, the researchers said.
“This campaign’s primary goal is to harvest usernames, passwords, and – in its more recent iteration – other information like IP address and location, which attackers use as the initial entry point for later infiltration attempts,” the researchers wrote, noting that in previous comments about the phishing campaign, the “components include information about the targets, such as their email address and company logo. Such details enhance a campaign’s social engineering lure and suggest that a prior reconnaissance of a target recipient occurs.”
Invoice-Themed Lures
The cybercriminals are using invoice themes with financial messages to lure people into clicking on the emails and the contained HTML files, like “XLS.HTML” to prepare the users to expect an Excel file. The attachments themselves contain several segments. There are JavaScript files that are used to steal passwords, which are then encoded. Over time, the hackers have moved from using plaintext HTML code to using other coding techniques – such as Morse code and other encryption methods – to hide the segments, the researchers wrote.
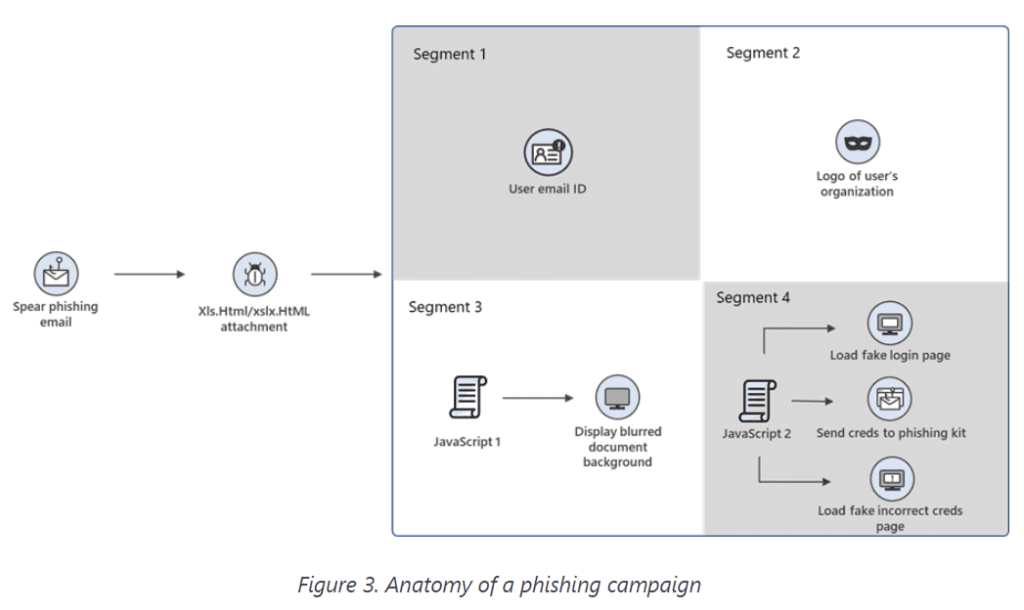
Some of the code segments are housed in various open directories – rather than in the attachments themselves – and are called by encoded scripts.
“This phishing campaign exemplifies the modern email threat: sophisticated, evasive, and relentlessly evolving,” the Microsoft researchers wrote. “In effect, the attachment is comparable to a jigsaw puzzle: on their own, the individual segments of the HTML file may appear harmless at the code level and may thus slip past conventional security solutions. Only when these segments are put together and properly decoded does the malicious intent show.”
The emails mimic regular financial-related business transactions, in particular sending what appears to be vendor payment advice.
Further reading: Microsoft Security Under Scrutiny After Recent Incidents
Multiple Segments to Campaign
The segments include the email address of the target and a logo of the targeted user’s organization, giving the email the air of authenticity. (If a logo isn’t available, the Microsoft Office 365 logo is used instead.) When the user opens the attachment, a script loads an image of a blurred account, suggesting that the sign-in for entering the account has timed out. A dialog box is shown prompting the user to enter their password. When the user types in the password, an error message is shown.
While that is going on, the malware is stealing the user’s data.
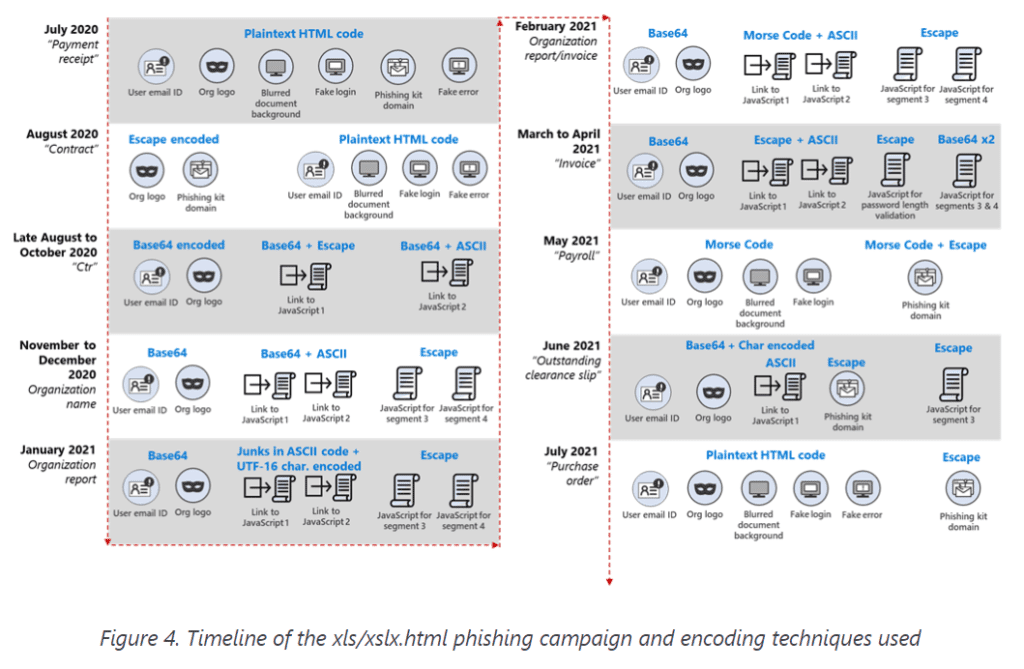
Attackers have created 10 iterations of the phishing campaign since Microsoft security researchers first came across it in July 2020. The lures have included such phrases as “payment receipt,” “payroll” and “contract.” The encoding evolved from plaintext HTML to other methods, such as Escape, Base64 and Morse code, which was used in February and May.
In May, the hackers included a new module that was used to grab the user’s IP address and country data, which were sent to a command-and-control server. This is the information that the bad actors could use in combination with usernames and passwords to their initial entry point in later attempts to get into systems.
Last month, another new twist was introduced. Using the term “purchase order” as the lure, malware no longer displayed a fake error message after the user typed their password, the researchers wrote. Instead, the phishing kit redirected the user to a legitimate Office 365 page.
Whitelisting vs. Blacklisting
The techniques used by the attackers highlight the ongoing debate between whitelisting and blacklisting, according to John Bambenek, threat intelligence advisor at IT and security operations company Netenrich.
“If we rely on blacklisting techniques, there are near infinite ways to obfuscate and code away detection of malicious behavior,” Bambenek told eSecurity Planet. “Ideally we should focus on detecting what is benign and anything outside of that – such as the use of Morse code outside the Ham radio operator course – should be flagged and/or blocked.”
Social Engineering Still a Problem
The attack detailed by Microsoft shows again how social engineering is the driver for such phishing campaigns and that only a little bit of personalization is needed to convince the target to share login credentials to corporate resources or to download a malicious app, Hank Schless, senior manager of security solutions at cybersecurity firm Lookout, told eSecurity Planet.
“This particular incident shows how attackers target individuals on particular cloud platforms, such as Microsoft Office, in order to steal corporate login credentials,” Schless said. “It’s not very complex for an attacker to build a web page that looks like a Microsoft login page and spoof the URL to appear legitimate at a quick glance. As soon as the target enters their login credentials, the attacker can use them and log in from their own device and access corporate resources.”
Because login credentials are often the same for all work applications, the attacker can not only use them for Microsoft Office but for other software-as-a-service (SaaS) and infrastructure-as-a-service (IaaS) applications to get access to a company’s most sensitive data, he said.
Schless noted that phishing campaigns can be particularly effective on mobile devices like smartphones and tablets, which have “simplified interfaces that hide many red flags indicative of phishing attacks. They can also deliver phishing links through email, SMS, social media platforms, third-party messaging apps, gaming and even dating apps.”
A Multi-Layered Approach Needed
A key defense is using a cloud access security broker (CASB) solution that can detect anomalous logins and activity, which could indicate an account has been compromised. If a user who normally logs in from New York suddenly does so from Moscow a few minutes later, the solution can revoke the employee’s access and prevent attackers from stealing data or launching a ransomware attack, he said.
The Microsoft researchers also recommended a comprehensive approach given the highly evasive and fast-evolving nature of the threat. This would include multi-layered and cloud-based machine learning models and dynamic analysis to inspect emails and attachments and determine the reputation of both the message sender and recipient. Built-in sandboxes can examine files and URLs to determine if they’re malicious.
“For this phishing campaign, once the HTML attachment runs on the [Microsoft Defender for Office 365] sandbox, rules check which websites are opened, if the JavaScript files decoded are malicious or not, and even if the images used are spoofed or legitimate,” they wrote.








