Last summer, a wave of sextortion emails began flooding inboxes around the world. The spammers behind this scheme claimed they’d hacked your computer and recorded videos of you watching porn, and promised to release the embarrassing footage to all your contacts unless a bitcoin demand was paid. Now, French authorities say they’ve charged two men they believe are responsible for masterminding this scam. One of them is a 21-year-old hacker interviewed by KrebsOnSecurity in 2017 who openly admitted to authoring a banking trojan called “Nuclear Bot.”

On Dec. 15, the French news daily Le Parisien published a report stating that French authorities had arrested and charged two men in the sextortion scheme. The story doesn’t name either individual, but rather refers to one of the accused only by the pseudonym “Antoine I.,” noting that his first had been changed (presumably to protect his identity because he hasn’t yet been convicted of a crime).
“According to sources close to the investigation, Antoine I. surrendered to the French authorities at the beginning of the month, after being hunted down all over Europe,” the story notes. “The young Frenchman, who lived between Ukraine, Poland and the Baltic countries, was indicted on 6 December for ‘extortion by organized gang, fraudulent access to a data processing system and money laundering.’ He was placed in pre-trial detention.”
According to Le Parisien, Antoine I. admitted to being the inventor of the initial 2018 sextortion scam, which was subsequently imitated by countless other ne’er-do-wells. The story says the two men deployed malware to compromise at least 2,000 computers that were used to blast out the sextortion emails.
While that story is light on details about the identities of the accused, an earlier version of it published Dec. 14 includes more helpful clues. The Dec. 14 piece said Antoine I. had been interviewed by KrebsOnSecurity in April 2017, where he boasted about having created Nuclear Bot, a malware strain designed to steal banking credentials from victims.
My April 2017 exposé featured an interview with Augustin Inzirillo, a young man who came across as deeply conflicted about his chosen career path. That path became traceable after he released the computer code for Nuclear Bot on GitHub. Inzirillo outed himself by defending the sophistication of his malware after it was ridiculed by both security researchers and denizens of the cybercrime underground, where copies of the code wound up for sale. From that story:
“It was a big mistake, because now I know people will reuse my code to steal money from other people,” Inzirillo told KrebsOnSecurity in an online chat.
Inzirillo released the code on GitHub with a short note explaining his motivations, and included a contact email address at a domain (inzirillo.com) set up long ago by his father, Daniel Inzirillo.
KrebsOnSecurity also reached out to Daniel, and heard back from him roughly an hour before Augustin replied to requests for an interview. Inzirillo the elder said his son used the family domain name in his source code release as part of a misguided attempt to impress him.
“He didn’t do it for money,” said Daniel Inzirillo, whose CV shows he has built an impressive career in computer programming and working for various financial institutions. “He did it to spite all the cyber shitheads. The idea was that they wouldn’t be able to sell his software anymore because it was now free for grabs.”
If Augustin Inzirillo ever did truly desire to change his ways, it wasn’t clear from his apparent actions last summer: The Le Parisien story says the sextortion scams netted the Frenchman and his co-conspirator at least a million Euros.
In August 2018, KrebsOnSecurity was contacted by a researcher working with French authorities on the investigation who said he suspected the young man was bragging on Twitter that he used a custom version of Nuclear Bot dubbed “TinyNuke” to steal funds from customers of French and Polish banks.
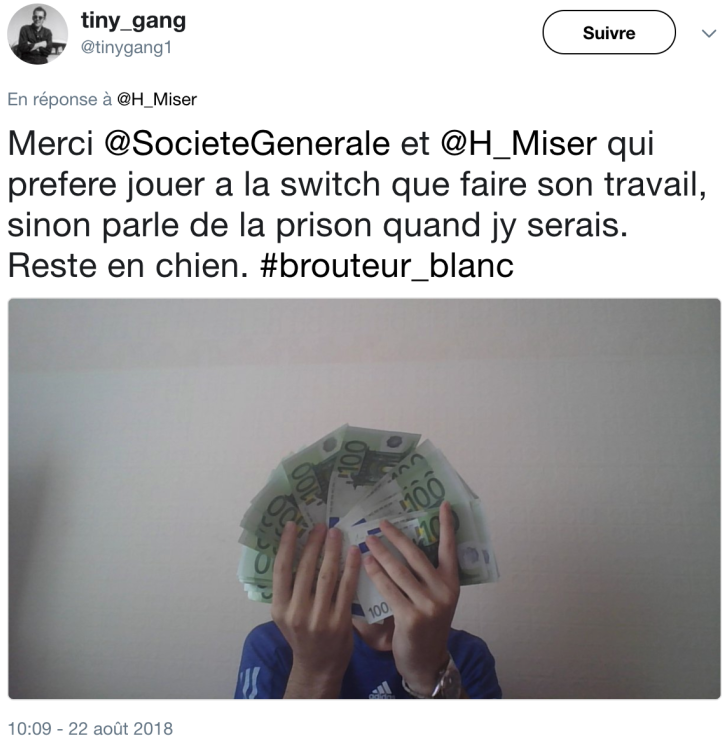
The source said this individual used the now-defunct Twitter account @tiny_gang1 to taunt French authorities, while showing off a fan of 100-Euro notes allegedly gained from his illicit activities (see image above). It seemed to the source that Inzirillo wanted to get caught, because at one point @tiny_gang1 even privately shared a copy of Inzirillo’s French passport to prove his identity and accomplishments to the researcher.
“He modified the Tinynuke’s config several times, and we saw numerous modifications in the malware code too,” the source said. “We tried to compare his samples with the leaked code available on GitHub and we noticed that the guy actually was using a more advanced version with features that don’t exist in the publicly available repositories. As an example, custom samples have video recording functionality, socks proxy and other features. So the guy clearly improved the source code and recompiled a new version for every new campaign.”
The source said the person behind the @tiny_gang Twitter account attacked French targets with custom versions of TinyNuke in one to three campaigns per week earlier this year, harvesting French bank accounts and laundering the stolen funds via a money mule network based mostly in the United Kingdom.
“If the guy behind this campaign is the malware author, it could easily explain the modifications happening with the malware, and his French is pretty good,” the researcher told KrebsOnSecurity. “He’s really provocative and I think he wants to be arrested in France because it could be a good way to become famous and maybe prove that his malware works (to resell it after?).”
The source said the TinyNuke author threatened him with physical harm after the researcher insulted his intelligence while trying to goad him into disclosing more details about his cybercrime activities.
“The guy has a serious ego problem,” the researcher said. “He likes when we talk about him and he hates when we mock him. He got really angry as time went by and started personally threatening me. In the last [TinyNuke malware configuration file] targeting Poland we found a long message dedicated to me with clear physical threats.”
All of the above is consistent with the findings detailed in the Le Parisien report, which quoted French investigators saying Antoine I. in October 2019 used a now-deleted Twitter account to taunt the authorities into looking for him. In one such post, he included a picture of himself holding a beer, saying: “On the train to Naples. You should send me a registered letter instead of threatening guys informally.”
The Le Parisien story also said Antoine I. threatened a researcher working with French authorities on the investigation (the researcher is referred to pseudonymously as “Marc”).
“I make a lot more money than you, I am younger, more intelligent,” Antoine I. reportedly wrote in July 2018 to Marc. “If you do not stop playing with me, I will put a bullet in your head. ”
French authorities say the defendant managed his extortion operations while traveling throughout Ukraine and other parts of Eastern Europe. But at some point he decided to return home to France, despite knowing investigators there were hunting him. According to Le Parisien, he told the French authorities he wanted to cooperate in the investigation and that he no longer wished to live like a fugitive.




FIRST!!!!! Awesome article Krebs!
“He’s really provocative and I think he wants to be arrested in France because it could be a good way to become famous and maybe prove that his malware works ”
Little “Pepe Le Pew” here is a full blown narcissist at such a young age.
Nice coincidence. Just today got ten+ reports from my users about sextorsion e-mails. Written in Russian, sent to addresses of ex-USSR subsidiaries of big international company.
While this guy may have been behind a French version of the scam, I don’t see anything in the Le Parisien article that would demonstrate he is the mastermind of the sextortion scam, itself. The sextortion scam actually started as early as late 2017 (https://nexusconsultancy.co.uk/blog/email-scam-ashamed-of-yourself/), and I covered it back in March of 2018 as it became more widespread (https://www.techlicious.com/blog/is-the-porn-blackmail-scam-real/). Yet the Le Parisien article says that Antoine I.’s campaign started in “January” (presumably, January 2019). And while the French emails were written in “impeccable French”, the English versions have been in anything but impeccable English (Antoine was born in the US and has looked at jobs in the US, so presumably his English isn’t that bad).
Perhaps this is his ego speaking, once again, behind claims of being the “inventor” of this scam, rather than just another follower.
I keep thinking that if I felt like tracking down the idiots, I’d love to talk to them. I mean, I am *so* TERRIFIED of someone who has a username of “nightmare”, and they’ve gotten m videos….
Really? So, they got into my house, and connected my Sony *camera* to my computer, and their software works on Linux?
That’s the whole point of these sextortion emails. There are times where no one actually got hacked or has malware on their system. It’s a lie to get people scared into giving them what they want. I’ve seen ones that were like, “We installed malware on your system and have been watching you look at porn. You’ve got some weird fetishes. We took videos of you watching it and we’ll release it to the public if you don’t pay us . You have !” The average person that reads that more than likely will not fall for it, but think of how many people actually watch porn and do have weird fetishes that an email like that would apply to. If you think about it, something like that can be more effective for the “attackers”, if you want to call them that, because they don’t even have to do anything but blast out an email.
It’s a product of how porn watching has evolved.
Is anyone reading magazines anymore? What about VHS or DVDs? No? What about desktop systems with a USB camera that the user set up manually and is quite aware of its existence?
What about laptops which nearly ALL have built in cameras? Now we are getting to the vast majority of people. And now people watch on their phones… which ALL have cameras that face the front.
Its a probability game for them. They know that 99% of men watch porn, and today, 95% of them watch on a device with a camera… and if just a few of them are paranoid enough, then they might have to assume they got malware that caught them.
Camera hijacking is very common… and until I got a phone with a pop up front camera, I had no idea how often a website would turn on the front camera.
There is no indicator light on phone cameras… and the permissions are usually misconfigured. So the user has no idea.
Having a popup camera is awesome. No notch is a benefit too. But malicious web site code that turns on the camera can’t do so without being detected now.
I’ve already caught the uhaul website turning on my camera for some reason.
I get those all the time. In my case they cracked an old weak password that I used more than 15 years ago, and are using that to “prove” that they cracked my account.
They also use the old trick of forged SMTP “From” headers to “prove” that they hacked my email.
It may be in some way related to twitter as well – some of the emails address me by my twitter handle and not my actual name.
Bjorn, we’ve documented many of these fake threats on our blog at The Daily Scam. In fact, we get dozens of these threats ourselves! Of course, they are all completely bogus and use scare tactics to trick someone into paying bitcoins. But some are very clever, having connected old passwords to email accounts from stolen passwords. Visit: https://www.thedailyscam.com/phone-malware-recording-you/
One thing to think about. If the scam did not make them a profit, it would have died out a long time ago.
Hey, can we plan some article that he was posting crap about Putin and then send him back to Ukraine? We’ll see how well that airhead thinks about Western society after that.
LOL Great idea. We should do that to all the crooks that are hard to punish properly due to pathetic laws that encourage these scum. (by encourage, I mean light punishment and they most often have a life time of funds stashed in multiple countries) thus a couple years (at most in the EU) and they live like a king after. not cool.
So Augustin is Antoine? Is there proof of it?
We got some of these sextortion e-mails. The nothing for some time. Now we are getting similar ones but in russian and about hacked devices. https://pastebin.com/ncLd9Lr7
> The Le Parisien story says the sextortion scams netted the Frenchman and his co-conspirator at least a million Euros.
Sad that so many fell for the scam.
The sample email in the linked article names a price of $1400. That would make for 800+ paying victims.
I hope Mr. Krebs gets to take a well deserved Christmas break. But given the dysfunction out there I suspect not.
I am doing a research project which requires that I compile feedback on how difficult it is to get a job in Cybersecurity. It is my hope that the results of this project produce substantive change. I want to contribute to the solution.
Hopefully Brian will send people my way. Or drop a comment here.
Have a Happy Holiday Brian. May the force be with you.
There are males who are terrified that people will know they watch porn??
You should get out more often dude.
More than half of women do too. It’s like we were built for this kind of thing or something. :b
I received eight sextortion emails in my work email during the past three months or so. All were in English language. To me some sentences resembled the style African scammers use. A follow-up of the bitcoin addresses in the emails showed a total ~ $80,000 in BTC deposits to the scammers’ addresses. Values of many individual deposits matched the amount requested in the emails. There were some small deposits which could have been test transfers. I am assuming there were real people who paid these scammers.
My friend, he is true, researchers allways put their nose somewhere where is not place for them..
I know many guys from old or news scene and no one like that..
If they target a bigger group with ease budget of 100k$ don’t be suprised if they receve shots..
Like it was the case many time, researchers was killed bullet in head in his house and no suspect was ever found..
So stop playing with that, stop before you will be next victim..
Just telling