Ransomware attackers, who use myriad methods to get their malware into the systems of businesses large and small in hopes of pulling down millions of dollars, are now going directly to the source.
A researcher with email security solutions vendor Abnormal Security found a threat actor directly emailing employees of a company urging them to release the ransomware into a company computer or Windows server in return for 40 percent – about $1 million – of the expected $2.5 million ransom the company would pay.
The hope was that one of the emails would hit the inbox of a disgruntled employee who would be willing to turn his displeasure into a payday that would help him and the cybercriminal.
“Historically, ransomware has been delivered via email attachments or, more recently, using direct network access obtained through things like unsecure VPN accounts for software vulnerabilities,” Crane Hassold, director of threat intelligence at Abnormal Security, wrote in a blog post. “Seeing an actor attempt to use basic social engineering techniques to convince an internal target to be complicit in an attack against their employer was notable.”
Evolving Ransomware Scene
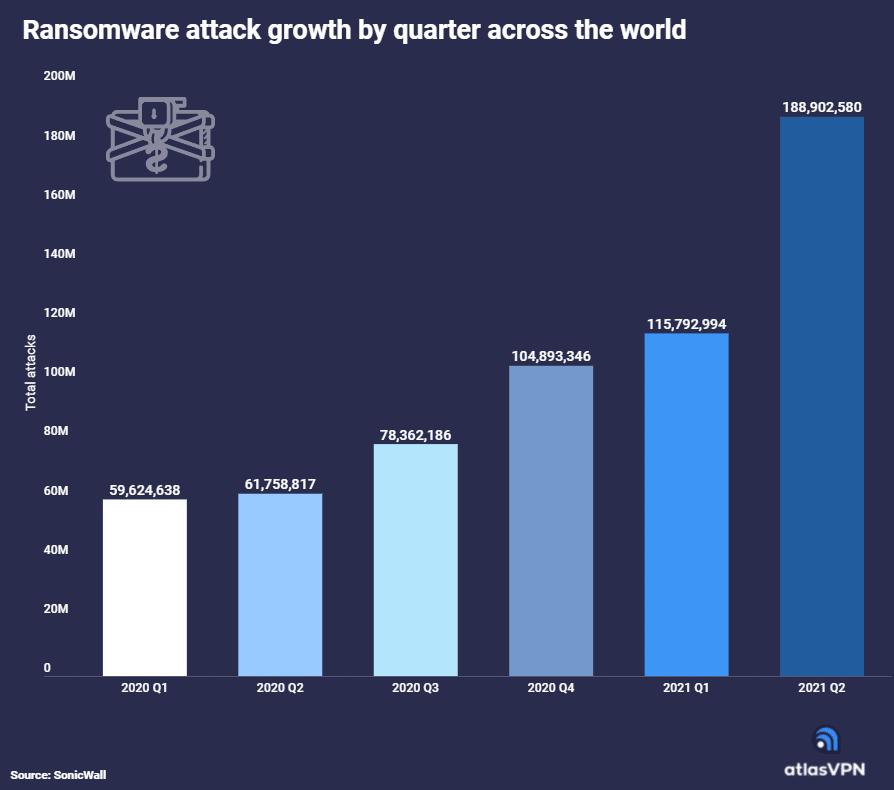
The case of a direct approach to company employees is the latest illustration of the ever-evolving and fluid nature of a ransomware landscape that has become a key threat to organizations around the world. According to a report this week by Atlas VPN, the number of ransomware attacks in the first half of 2021 have jumped year-over-year by 151 percent, with the United States being the most targeted country by a wide margin. The numbers in the report come from cybersecurity vendor SonicWall.
There were 304.7 million ransomware attacks in the first six months of 2021, compared with 121.5 million during the same period last year. This year, 227.3 million of those attacks occurred in the United States.
“The number is concerning considering only half of the year has passed and we already know it is the worst result yet,” the researchers wrote. “Ransomware has continued to soar because more businesses are willing to pay a ransom to get their data back. That lets hackers know that their methods are working and launching attacks will allow them to earn a quick buck.”
Fortinet’s midyear threat landscape report released today found that ransomware activity is up tenfold from a year ago.
Filling the Void
The shutting down of operations by ransomware groups like REvil and DarkSide also has given other bad actors room to roam, which has fueled a resurgence in the LockBit ransomware-as-a-service (RaaS), with the most recent high-profile attack being on global consulting firm Accenture that sought a ransom of about $50 million. Organizations in such countries as Italy, Taiwan and the UK also have been targeted by LockBit 2.0, the latest version of the ransomware, according to a report this week by cybersecurity vendor TrendMicro. LockBit attackers have also looked for inside help by installing wallpaper on compromised PCs offering a cut of ransomware payments for people inside companies providing access to a system.
In the case involving Abnormal Security, Hassold said the vendor’s technologies identified and blocked messages sent to several of the vendor’s customers from a bad actor making the offer to senior executives. In the message sent, the bad actor implied he had ties to the DemonWare ransomware group. The malware, which also is known as Black Kingdom and DEMON, has been around for a few years and is available for free on GitHub.
Further reading: How Zero Trust Security Can Protect Against Ransomware
Conversation with a Bad Actor
The email also gave two ways a person interested in the offer could contact the bad actor, either through Outlook mail or the Telegram social media platform. Hassold did, creating a fictitious profile and then reaching out via Telegram.
Over the course of several days of online conversation, Hassold was able to talk the person into sending what turned out to be a file named “Walletconnect (1).exe” containing the ransomware. The amount of the planned ransom demand changed, dropping from $2.5 million to as low as $120,000.
Regarding the ransomware, “at one point in the conversation, we asked the actor if he had created the ransomware himself or if he was just using it. The actor told us that he ‘programmed the software using python language,’” he wrote in the blog post. “In reality, however, all of the code for DemonWare is freely available on GitHub. … In this case, our actor simply needed to download the ransomware from GitHub and socially engineer someone to deploy the malware for them.”
The use of the DemonWare malware “demonstrates the appeal of ransomware-as-a-service, as it lowers the barrier of entry for less technically-sophisticated actors to get into the ransomware space,” Hassold wrote.
The bad actor told Hassold that he initially sent senior-level executives at the targeted companies phishing emails in hopes of compromising their accounts, but after that failed, he turned to trying to lure employees to unleash the ransomware themselves.
Threat Traced to Nigeria
Eventually Abnormal Security was able to link the email to a person in Nigeria who told Hassold that he was working to build a social network called Sociogram, going as far as giving Abnormal Security a link to his LinkedIn page.
“Knowing the actor is Nigerian really brings the entire story full circle and provides some notable context to the tactics used in the initial email we identified,” Hassold wrote. “ For decades, West African scammers, primarily located in Nigeria, have perfected the use of social engineering in cybercrime activity. While the most common cyber attack we see from Nigerian actors (and most damaging attack globally) is business email compromise (BEC), it makes sense that a Nigerian actor would fall back on using similar social engineering techniques, even when attempting to successfully deploy a more technically sophisticated attack like ransomware.”
In a blog post, security threat researcher Chris Krebs wrote that “cybercriminals trolling for disgruntled employees is hardly a new development. Big companies have long been worried about the very real threat of disgruntled employees creating identities on darknet sites and then offering to trash their employer’s network for a fee.”
Krebs added that “several established ransomware affiliate groups that have recently rebranded under new banners seem to have done away with the affiliate model in favor of just buying illicit access to corporate networks.”
John Hellickson, cyber executive advisor at cybersecurity consultancy Coalfire, told eSecurity Planet trawling for disgruntled employees “is an interesting and creative tactic to go after another potential weak link in an organization’s security defenses, but it’s not necessarily new. It’s hard to know how often this tactic has been used, but it’s not as prevalent as simple phishing or targeted attacks that have less human-to-human interactions to get a desired malicious outcome.”
This probably won’t be a significant contributor to the insider threat calculation now, but “it shouldn’t be discounted as something that couldn’t happen at any given organization.”
Yaniv Bar-Dayan, co-founder and CEO of Vulcan Cyber, a specialist in vulnerability remediation, told eSecurity Planet that the tactic is a new twist on a time-tested approach, adding that “social engineering and phishing tactics are evolving and being utilized to fuel the access hackers need to access corporate networks. But this is just the start.”