Ransomware: Average Ransom Payment Drops to $137,000
Data Breach Today
JULY 26, 2021
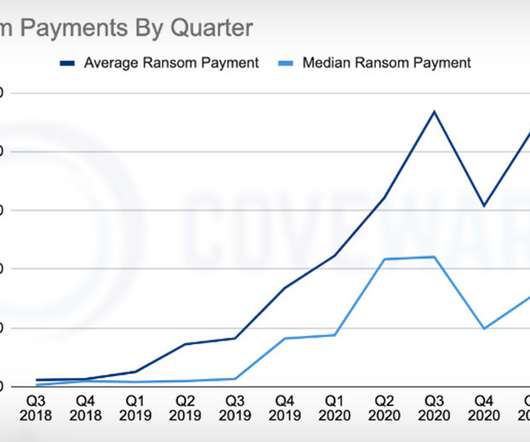
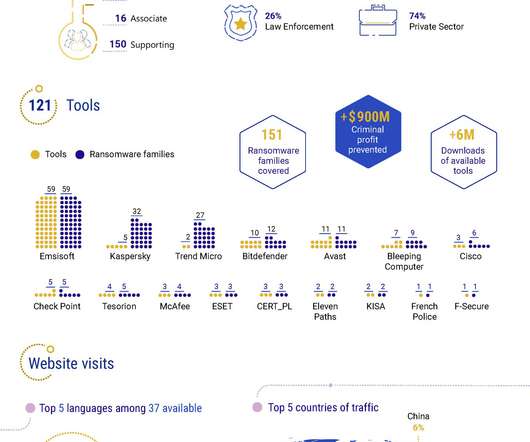
Fewer Victims Paying Attackers Simply to Delete Stolen Data, Coveware Reports Good news on the ransomware front: The average ransom paid by a victim dropped by 38% from Q1 to Q2, reaching $136,576, reports ransomware incident response firm Coveware. In addition, fewer victims are paying a ransom simply for a promise from attackers to delete stolen data.



































Let's personalize your content