Gaming Company Confirms Ragnar Locker Ransomware Attack
Data Breach Today
NOVEMBER 18, 2020
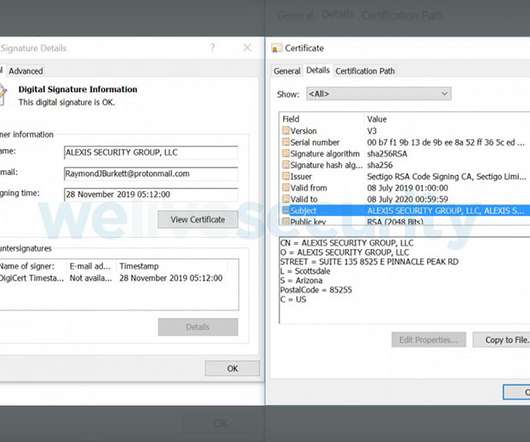
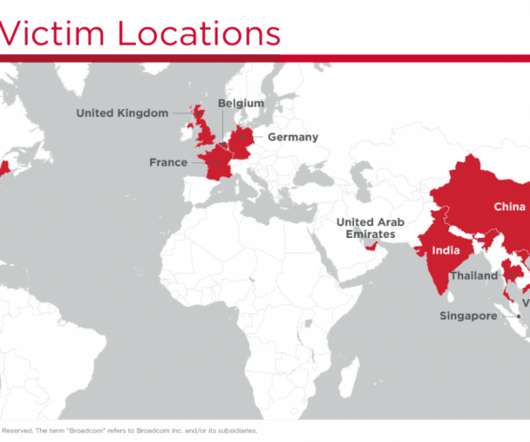
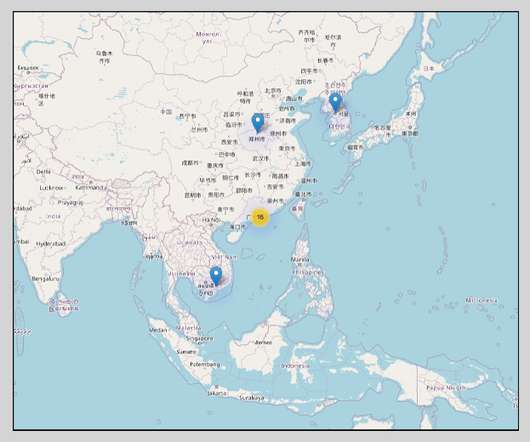
Capcom Says Over 350,000 Customer, Business Records Possibly Compromised Japanese computer game company Capcom acknowledged this week that a November security incident was a Ragnar Locker ransomware attack that resulted in about 350,000 customer and company records potentially compromised, including sales and shareholder data.



































Let's personalize your content