New Linux CronRAT hides in cron jobs to evade detection in Magecart attacks
Security Affairs
NOVEMBER 25, 2021
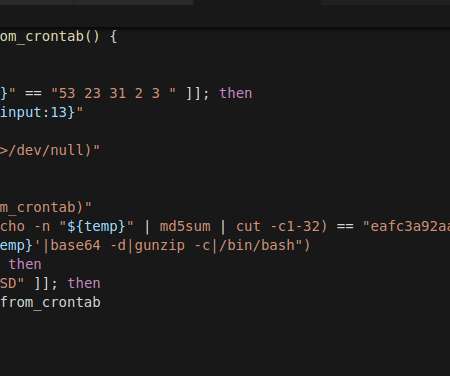
Security researchers discovered a new Linux RAT, tracked as CronRAT, that hides in scheduled cron jobs to avoid detection. Security researchers from Sansec have discovered a new Linux remote access trojan (RAT), tracked as CronRAT, that hides in the Linux task scheduling system (cron) on February 31st. Threat actors hides the malware in the task names, then the malicious code is constructed using several layers of compression and base64 decoding.


















Let's personalize your content