Details of a flaw in Apple’s Safari browser, publicly disclosed Tuesday, outline how the cybergang known as ScamClub reached 50 million users with a three-month-long malicious ad campaign pushing malware to mobile iOS Chrome and macOS desktop browsers.
The Safari bug, patched on Dec. 2 by Apple, was exploited by a malvertising campaign that redirected traffic to scam sites that flogged gift cards, prizes and malware to victims. Impacted was Apple’s Safari browser running on macOS Big Sur 11.0.1 and Google’s iOS-based Chrome browser. The common thread is Apple’s WebKit browser engine framework.
The attacks, which researchers at Confiant Security attributed to ScamClub, exploited a flaw in the open-source WebKit engine, according to a blog post published Tuesday by Eliya Stein, senior security engineer who found the bug on June 22, 2020.
He reports that the malicious campaign exploited a privilege-escalation vulnerability, tracked as CVE-2021–1801. Stein did not report how many, if any, people may have been impacted by the campaign or what type of malicious activity the threat actors may have engaged in post-exploit. Typically, a privilege-escalation attack’s primary goal is to obtain unauthorized access to a targeted system.
What is ScamClub?
ScamClub is a well-established cybergang that for the past three years has hijacked hundreds-of-millions of browser sessions with malvertising campaigns that redirect users to adult and gift card scams.
Until today, the group is best known for a massive 2018 campaign where it redirected 300 million users to shady phishing sites, serving up adult content and gift card scams.
Confiant dubbed the group ScamClub, because of the criminal’s use of multiple fast-changing redirection chains eventually spitting up shady gift-card offers and adult content.
ScamClub typically uses a “bombardment” strategy to flood ad-delivery systems with “tons of horrendous demand” rather than trying to obfuscate its nefarious activity, researchers note.
“They do this at incredibly high volumes in the hopes that the small percentage that slips through will do significant damage,” he explained.
What are the ScamClub Details of the WebKit Exploit?
In his Tuesday-report, Stein said this most recent ScamClub campaign redirected users to landing pages that offer prizes, such as “You’ve won a Walmart gift card!” or “You’ve won an iPhone!” to rather successful effect, he wrote.
Over the last 90 days alone, ScamClub has delivered over 50 million malicious impressions, “maintaining a low baseline of activity augmented by frequent manic bursts,” with as many as 16 million impacted ads being served in a single day, according to Stein.
This type of attack vector can be difficult for both the average person using the internet and businesses alike to handle, given the potential number of malicious ads being served, observed Saryu Nayyar, CEO of unified security and risk analytics firm Gurucul.
“Attacks like this can be a challenge to mitigate for home users, beyond keeping their patches up to date relying on an ISP provided or third-party service to block known malicious DNS domains,” she said in an email to Threatpost. “Organizations have a similar challenge with the sheer volume of malicious ads, but can benefit from enabling the same techniques and security analytics that can help identify malicious activities by their behaviors.”
Diary of a WebKit Exploit
The latest ScamCard payload has a number of steps to it, starting with an ad tag that loads a malicious Content Delivery Network-hosted dependency typically “obfuscated in absurd ways in attempt to evade URL blocklists” that can expand to thousands of lines of code, Stein wrote.
He said that Confiant researchers narrowed their investigation down to four lines of code that ultimately alerted them to ScamClub’s use of the WebKit bug in its campaign: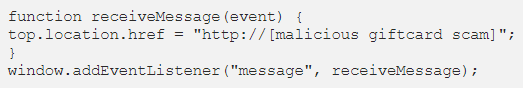 Observing that the code seemed different than a typical malvertising tactic of trying “to spray a bunch of redirect attempts in a single payload that try to do the redirect in different ways,” researchers investigated by staging a simple HTML file that implemented a cross-origin sandboxed frame and a button that dispatched their event.
Observing that the code seemed different than a typical malvertising tactic of trying “to spray a bunch of redirect attempts in a single payload that try to do the redirect in different ways,” researchers investigated by staging a simple HTML file that implemented a cross-origin sandboxed frame and a button that dispatched their event.
“The `allow-top-navigation-by-user-activation` sandbox attribute, which is often lauded as one of the most vital tools in an anti-malvertising strategy, should in theory prevent any redirection unless a proper activation takes place,” Stein explained. “Activation in this context typically means a tap or a click inside the frame.”
If this was the case, then Confiant’s proof of concept should not have been able to redirect the page. However, it did, which proved to researchers that ScamClub’s use of “a long tail iframe sandbox bypass” was leveraging a browser bug that turned out to be in WebKit, Stein said.
Is your small- to medium-sized business an easy mark for attackers?
Threatpost WEBINAR: Save your spot for “15 Cybersecurity Pitfalls and Fixes for SMBs,” a FREE Threatpost webinar on Feb. 24 at 2 p.m. ET. Cybercriminals count on you making these mistakes, but our experts will help you lock down your small- to mid-sized business like it was a Fortune 100. Register NOW for this LIVE webinar on Wed., Feb. 24.











