While Microsoft issued patches for the infamous BlueKeep vulnerability almost a year ago, researchers warn that almost half of connected medical devices in hospitals run on outdated Windows versions that are still vulnerable to the remote desktop protocol (RDP) flaw.
Researchers said they found that 22 percent of a typical hospital’s Windows devices were vulnerable to BlueKeep. Even worse, the number of connected medical devices running Windows that are vulnerable to BlueKeep is considerably higher — around 45 percent, they said. Vulnerable medical devices can include MRIs, ultrasounds, X-rays, and more, which run on operating systems — typically Windows – allowing their operators to more easily collect and upload data.
“For hospitals, the task of monitoring vulnerabilities, identifying affected devices, chasing down suitable patches, and distributing those patches across a sprawling campus is tedious, to say the least,” said researchers with CyberMDX in their “2020 Vision” report on medical security, released Tuesday. “This process is slow and inefficient, as the hospitals usually do not know which devices or security issues to attend to first.”
The BlueKeep flaw (CVE-2019-0708) was fixed during Microsoft’s May 2019 Patch Tuesday Security Bulletin. System administrators were urged to immediately deploy fixes as the flaw could pave the way for a similar rapidly-propagating attack on the scale of WannaCry. In the months following the disclosure of BlueKeep, researchers tracked a spike in scans for vulnerable systems and eventually active attacks exploiting the flaw.
Almost a year later, researchers have found that an alarming number of connected medical devices remain vulnerable to BlueKeep. The wormable implications of BlueKeep on medical devices are particularly concerning due to the hit that many hospitals took after attackers launched the 2017 WannaCry attack, interrupting several critical services at hospitals across England.
Beyond BlueKeep, outdated Windows versions are also exposing medical devices to an array of other vulnerabilities. For instance, up to 11 percent of connected medical devices are exposed to DejaBlue, a set of RDP flaws affecting Windows 7, Windows 8.1, and Windows 10 (as well as Windows Server 2008, Windows Server 2012, Windows Server 2016, and Windows Server 2019).
Medical Security Issues
So why haven’t organizations updated their medical devices? This is due to a variety of reasons. Patch management, for one, is a big issue for hospitals. Researchers said that four months after a major vulnerability is disclosed, most hospitals will still not have patched more than 40 percent of their vulnerable devices.
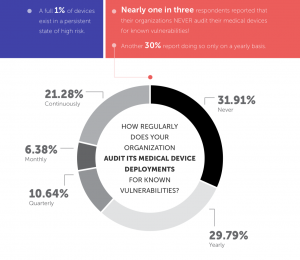
According to previous CyberMDX research, 80 percent of device manufacturers and healthcare orgs report that medical devices are “very difficult to secure,” citing a lack of knowledge and training on secure coding practices, and pressure on development teams to meet product deadlines. The study also pointed to a lack of quality assurance and testing procedures for medical devices, which lead to more vulnerabilities slipping by when products go to market. In fact, nearly one in three organizations surveyed by CyberMDX said that they never audit their medical devices for known vulnerabilities.
That’s no surprise to Charles Ragland, security engineer at Digital Shadows, who worked in emergency rooms and on ambulances as a paramedic for 10 years. During that time, he witnessed outdated medical devices first hand, including cardiac catheterization lab systems running on Windows Server 2003.
“With the level of complexity that involves managing networks with vast amounts of connected devices, it is not surprising that many of these devices have slipped through the cracks and remain vulnerable to threats such as BlueKeep,” Ragland told Threatpost. “As always, the most effective risk mitigation techniques involve turning off unnecessary services, implementing network level authentication [for RDP], blocking access to sensitive ports, and ensuring timely security updates.”
Chris Morales, head of security analytics at Vectra, told Threatpost that part of the problem also stems from a lack of accountability on the manufacturer, as devices are often brought in by medical staff and no one bothers to inform IT or security.
“Most medical devices are not updated as they serve a specific lifesaving function,” he told Threatpost. “While an OS update might seem benign, any interruption with the functioning of a medical device could have serious implications. Now this isn’t a total excuse for not updating. Manufacturers need update testing processes that enable to have a timeline for validation and updating.”
Medical devices continue to be discovered riddled with vulnerabilities. Earlier this month, Medtronic released updates to address known vulnerabilities in its line of connected medical devices that were initially disclosed last year and in 2018. In January, researchers found six vulnerabilities in a range of GE Healthcare devices for hospitals, which could allow attackers to disable the devices, harvest personal health information (PHI), change alarm settings and alter device functionality. In 2019, the Food and Drug Administration (FDA) issued an emergency alert, warning that Medtronic MiniMed insulin pumps are vulnerable to potentially life-threatening cyberattacks.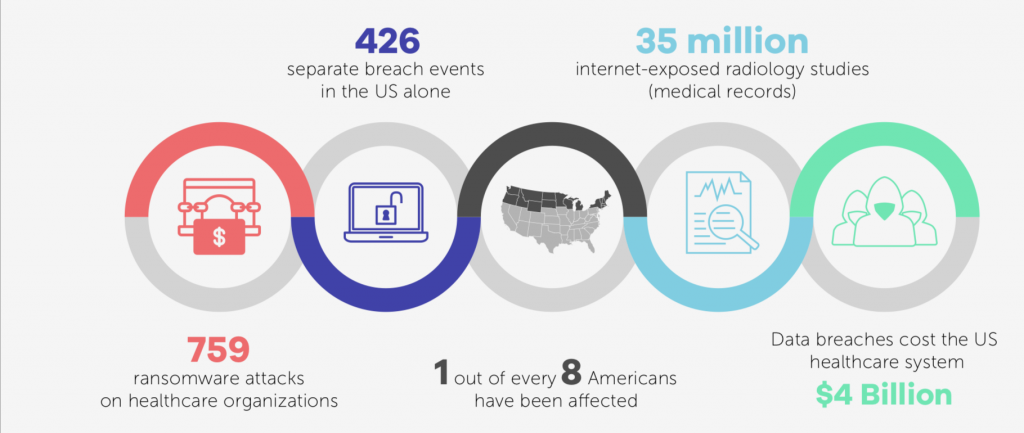
These security issues are leading to real-life attacks. In 2019, for instance, hospitals reported security incidents, from a server misconfiguration exposing data of 973,024 patients at UW Medicine, to phishing attacks compromising data at UConn Health and Oregon Department of Human Services; all the way up to full fledged ransomware attacks at the Columbia Surgical Specialist of Spokane, Sarrell Dental and Hospital Pavia Hato Rey.
Thomas Hatch, CTO and Co-Founder at SaltStack, told Threatpost that the security issues that the healthcare industry faces “is a tip of the iceberg problem, where the real vulnerabilities are much more vast than what we can even see.”
“IoT devices are notorious for being difficult to patch,” he told Threatpost. “The systems built around them are designed for, in this case, hospital medical staff, not maintenance. IoT devices get built for the target use case which makes them difficult to maintain because a single doctors’ office can be using many dramatically different devices; an entire hospital is even worse.”